Free CVSS 2.0 Calculator_
Find out how severe your security vulnerabilities are and how you should prioritize for remediation
Handling security vulnerabilities is one of the most challenging aspects in infosec. Just look at what industry statistics reveal:
- 90% of applications had at least one issue outside of the OWASP Top 10 in 2018 (2018 Application Security Research Update)
- 49% of tested apps had a critical or high-severity weakness that’s also outside the same OWASP Top 10 (2018 Application Security Research Update)
- In EMEA, for example, 42% of all cyber attacks focused on compromising web apps in 2018(ENISA Threat Landscape Report 2018)
- 64% of companies have zero visibility over 3rd party vulnerabilities (EY Global Information Security Survey 2018-2019)
That’s why we wanted to create a tool that helps you assess your weaknesses so you’ll know which one needs immediate solutions.
CVSSv2.js is a free and Open Source Javascript plugin based on the CVSSv2 algorithm and NIST tool. We worked to make it easier to share and deploy so companies like yours can use it more frequently.
Free Common Vulnerability Scoring System 2.0 Online Calculator FAQ
What is the Common Vulnerability Scoring System (CVSS)?
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard under the custodianship of NIST.
This particular system helps cyber security specialists and other IT professionals establish how severe a vulnerability is so they can prioritize remediation efforts.
The scores used by the CVSS are based on a series of metrics established through expert assessment. As a result, they are recognized and across the information security industry.
The scores range from 0 to 10.
Vulnerabilities with a base score in the range:
- 9.0 – 10.0 are Critical
- 7.0-9.0 are High
- 4.0-6.9 are Medium
- 0-3.9 are Low & Informational
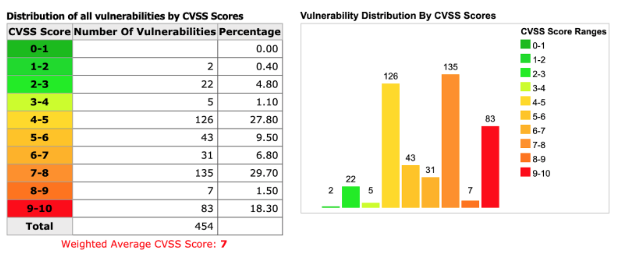
For example, here are the CVSS Scores for Google Android between March 29, 2018 and March 29, 2019:
What is a base score in CVSS?
A base score is assigned to a vulnerability by a vendor or originator. This score is assigned when the vendor or originator wants to publish the vulnerability and expects it to remain unchanged.
The score is calculated to include the CIA triad of information security: Confidentiality, Integrity and Availability.
The base score is then influenced by the Temporal and Environmental metrics but has the biggest influence on the final score.
The base score indicates the severity assigned to a specific vulnerability.
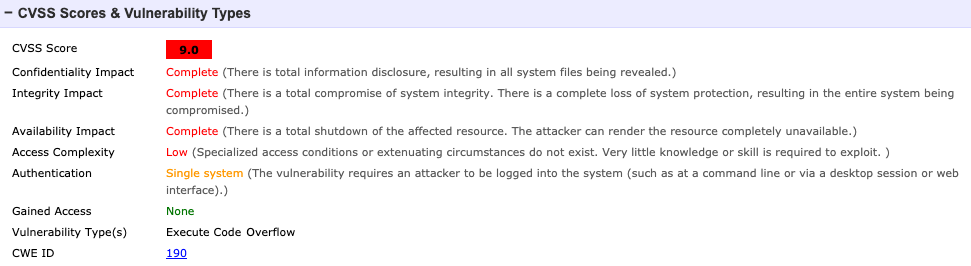
For example, here is one of the vulnerabilities included in the example above, pertaining to Google Android from the period between March 29, 2018 and March 29, 2019:
What is a temporal score metric in CVSS?
The temporal score metric indicates the time-dependent characteristics of a vulnerability. Such features include:
- How exploitable the vulnerability is
- If a solution or workaround is available or not
- How credible the vulnerability report is in terms of corroboration and instances that confirm the report.
What is a environmental score metric in CVSS?
The environmental score metric represents the potential damage the vulnerability can cause if exploited successfully.
Key aspects include:
- Collateral damage, such as potential loss of life or physical assets
- Target distribution which describes the volume of potential targets the vulnerability impacts
Impact requirement which highlights how critical the potentially affected IT asset can be to business operations overall.
How do you prioritize remediation actions according to the Common Vulnerability Scoring System (CVSS)?
Here’s how you can interpret your risk level according to results generated by the CVSS online calculator so you can address the most dangerous vulnerabilities.
- For critical vulnerabilities (CVSS 9-10), take immediate action to mitigate them through patching or fixes the situation warrants
- For high vulnerabilities (CVSS 7-8.9), establish a plan to address them within the near future (no more than a couple of weeks)
- For medium vulnerabilities (CVSS 4-6.9), set up a deadline to solve them within a reasonable period of time, depending on available resources
- For low vulnerabilities (CVSS 2-3.9), decide if you’re willing to accept the risk or take certain mitigation actions
- For information vulnerabilities (CVSS 0-1.9) you don’t have to do anything, their purpose being to acknowledge their existence
Corrective actions to patch vulnerabilities can include software or hardware updates, security awareness training or even new or improved policies and processes that favor better cyber security.
Please take into account that CVSS is not capable of assessing the potential combined effect of vulnerabilities exploited in a chain sequence. As a consequence, severity levels described by the CVSS are perfectly accurate as potential impact and fallout depends on your organisation’s particularities.
What are the main differences between CVSS2 vs CVSS3?
The new CVSS calculator, dubbed CVSS3, introduces a series of changes that broaden the information spectrum provided about web application vulnerabilities, which are one of the most frequent targets for cybercriminals.
CVSS3 introduces new metrics, such as Scope (S) and User Interaction (UI). It also changes old metrics such as Authentication (Au) into newer ones such as Privileges Required (PR).
These new details help provide more context for better decision-making when it comes to managing vulnerabilities in organisations.
However, most cybersecurity professionals still prefer to use CVSS v2 mainly because is the most popular scoring mechanism used by many advanced tools and online reporting applications.
Moreover, the majority of vulnerabilities reported in the past have only the CVSS v2 score calculated. As a result, it is still unreliable to get a clear overview in the 3rd version of Common Vulnerability Scoring System.
How can I embed the CVSS calculator on my own website?
If you’re interested in embedding this free Common Vulnerability Scoring System calculator into your own website, please follow the instructions included in the dedicated GitHub repository.
Try out these other security tools
At Bit Sentinel, we like to use our experience and know-how to make security simpler and more effective for you and everyone who needs this. That’s why we also created: