Bit Sentinel Expertise and Certifications_
Cybersecurity is not a job for us, it’s a way of life.
Everything we do focuses on following through on our responsibility to secure and protect the integrity of your company’s communication networks and information technology systems.
We’re relentless learners, constantly broadening our knowledge and exploring technical depth and challenges.
We do so because we believe an information security professional must have a well-rounded experience, both in terms of tech skills and business knowledge. We’re always up for a challenge that involves a multidisciplinary approach!
We choose to work with customers on a low-volume basis to deliver uncompromised service quality, as our engagements are more like long term partnerships.
This is what we enjoy doing: creating a more secure context for businesses to thrive and serve their customers well.
Bit Sentinel Certifications_
Our core belief is that education and knowledge are essential to evolution. This is why our team is made of highly qualified experts who hold the most prestigious professional certificates in the field.
Obtaining these globally recognized standards of achievement is how we follow through on our commitment to constantly increased our layer of expertise.
This enables us to apply our skills and know-how to a wide range of information security challenges and playing fields.
OSCE | Offensive Security Certified Expert.
The Offensive Security Certified Expert (OSCE) features an extremely challenging exam.
During the exam, students are required to:
- demonstrate their comprehension of the material directly covered in the CTP course
- prove they fully grasp the underlying concepts presented throughout the course
- demonstrate they can apply them in unknown situations.
The OSCE exam challenges the students to prove they have a clear and practical mastery of advanced penetration testing skills through an arduous 48 hour certification exam.
The OSCE exam consists of a dedicated vulnerable network, designed to be compromised within a 48-hour time period.
The exam is exclusively hands-on and completion represents submitting an in-depth penetration test report of the OSCE examination network.
The coveted OSCE certification is awarded to students who successfully gain administrative access to systems on the target network.
OSCP | Offensive Security Certified Professional.
The Offensive Security Certified Professional (OSCP) is the world’s first completely hands-on offensive information security certification.
The OSCP challenges students to prove they have a clear and practical understanding of the penetration testing process and lifecycle through an arduous twenty four (24) hour certification exam.
The OSCP exam consists of a dedicated vulnerable network, designed to be compromised within a 24-hour time period.
The exam is entirely practical and to complete it, the student must submit an in-depth penetration test report of the OSCP examination network and PWK labs.
The coveted OSCP certification is awarded to students who successfully gain administrative access to systems on the vulnerable network.
OWSP | Offensive Security Wireless Professional.
The Offensive Security Wireless Professional (OSWP) is the only practical wireless attacks certification in the security field today.
The OSWP requires students to prove they have the practical ability to perform 802.11 wireless audits using open source tools through a hands-on, four (4) hour, certification exam.
The OSWP exam consists of several dedicated wireless networks with various configurations and vulnerabilities. The student is tasked with identifying, analyzing, and attacking each of the wireless networks presented to them. The ultimate goal is to gain access to the network encryption keys.
The student must submit the correct encryption codes for all networks, as well as the attack vectors used to obtain them in order to be awarded the OSWP certification.
Send us a messageCISA | Certified Information Systems Auditor.
Certified Information Systems Auditor (CISA) is a globally recognized certification in the field of audit, control, and security of information systems.
The CISA gained worldwide acceptance due to its uniform certification criteria.
This particular certification has a high degree of visibility and recognition in the fields of IT security, IT audit, IT risk management, and governance. Professional requirements for open roles in IT security management, IT audit or IT risk management often include having a CISA certification.
The certification is extremely challenging and is associated with a high failure rate.
The CISA is awarded by ISACA (previously Information Systems Audit and Control Association), one of the strictest enforcers of high standards in the infosec industry.
CISSP | Certified Information Systems Security Professional.
The CISSP® certification is a globally recognized standard of achievement that confirms an individual’s knowledge in the field of information security.
CISSPs are information assurance professionals who define the architecture, design, management and/or controls that assure the security of business environments.
This was the first certification in the field of information security to meet the stringent requirements of ISO/IEC Standard 17024.
The CISSP exam tests one’s competence in the 10 CISSP domains of the (ISC)²® common body of knowledge (CBK®), which cover critical topics in security today, including:
- risk management
- cloud computing
- mobile security
- application development security and more.
Candidates must have a minimum of 5 years of paid full-time work experience in 2 of the 10 domains.
It takes a wide breadth of knowledge and extensive experience to pass the exam and this is what sets the CISSP apart across the industry.
Get in TouchGPEN | GIAC* Penetration Tester.
The GPEN certification is for security personnel whose job duties involve assessing target networks and systems to find security vulnerabilities. Certification objectives include:
- penetration-testing methodologies
- the legal issues surrounding penetration testing
- how to properly conduct a penetration test
- best practices concerning technical and non-technical techniques that are specific to conducting penetration tests.
The GPEN is one of the key Global Information Assurance Certifications an infosec professional can be awarded based on his performance.
eCCPT | eLearnSecurity Certified Professional Penetration Tester.
The eCPPT designation stands for eLearnSecurity Certified Professional Penetration Tester.
The eCPPT is a 100% practical and highly respected Ethical Hacking and Penetration Testing Professional certification counting certified professional on all the five continents.
By obtaining the eCPPT Gold, we achieved recognition for our skills in the following areas:
- Penetration testing processes and methodologies
- Vulnerability Assessment of Networks
- Vulnerability Assessment of Web Applications
- Advanced Exploitation with Metasploit
- Performing Attacks in Pivoting
- Web application Manual exploitation
- Information Gathering and Reconnaissance
- Scanning and Profiling the target
- Privilege escalation and Persistence
- Exploit Development
- Advanced Reporting skills and Remediation.
LPIC-1.
LPIC-1 is the first certification in LPI’s multi-level Linux Professional certification program.
The LPIC-1 confirms our ability to:
- perform maintenance tasks using the command line
- install and configure a computer running Linux
- configure basic networking.
LPIC-2.
The LPIC-2 is the second certification in LPI’s multi-level professional certification program.
The LPIC-2 validates our ability to manage small to medium–sized mixed networks with all their interdependencies and specificities.
ICWOD | Introduction to Cyber Warfare and Operations Design.
“Introduction to Cyber Warfare and Operations Design” is an approved course by The University of Fairfax (USA) and it carries a .5 credit toward a Masters or Doctorate degree from The University of Fairfax.
The University of Fairfax is an accredited, cybersecurity graduate university which seeks to address the growing shortage of
cybersecurity professionals who can conduct cutting-edge research.
The University of Fairfax offers online graduate programs with curricula exclusively focused on cybersecurity.Founded in response to 9/11, the University of Fairfax is accredited by the Accrediting Commission of the Distance Education and Training Council (DETC).
The Accrediting Commission of DETC is listed by the U.S. Department of Education as a nationally recognized accrediting agency and is a recognized member of the Council for Higher Education Accreditation (CHEA).
The University of Fairfax has been certified by the State Council of Higher Education in Virginia (SCHEV) to operate in the state of Virginia.
The University of Fairfax is an Authorized Education Partner and CPE Provider of (ISC) ®, and has received National Security Agency (NSA) authorization for awarding both the NSA 4011 and 4012 certifications.
Completing this course confirms our ability to assist our customers when dealing with cyber warfare operations and tactics.WSNIC | Windows Server 2008 Network Infrastructure Configuration.
The Windows Server 2008 Network Infrastructure Configuration exam evaluate our ability to accomplish the following technical tasks:
- Configuring addressing and services (21%)
- Configuring names resolution (22%)
- Configuring network access (18%)
- Configuring file and print services (20%)
- Monitoring and managing a network infrastructure (20%).
The Microsoft Certified Technology Specialist (MCTS) on Windows Server 2008 credentials are intended for information technology (IT) professionals who work in the complex computing environment of medium to large companies.
The MCTS candidate should have at least one year of experience implementing and administering Windows Server 2008 R2 in an environment that has:
- 250 to 5000 or more users
- Multiple physical locations
- Multiple domain controllers
- Network services and resources such as messaging, databases, file and print, firewalls, Internet access, an intranet, Public Key Infrastructure, remote access, remote desktop, virtualisation, and client computer management
- Connectivity requirements such as connecting branch offices and individual users in remote locations to corporate resources and connecting corporate networks.
Security Awareness & Community Projects_
Bit Sentinel is always keen to stay close to the community and give back! This is why yearly, the team is involved in different community events or organizing CTF competitions to encourage and teach younger generations about ethical hacking.
Whenever the time allows it, Bit Sentinel supports initiatives that have the potential to become important development factors to the local security landscape.
Here are some of the projects we are actively involved:
DefCamp
In 2019, DefCamp turns 10. What started as a small community event, turned into one of the biggest hacking and information security conferences in the CEE. With almost 2000 attendees in 2018, the team is constantly working to attract skilled individuals to cybersecurity roles and guide those already on this professional path.
The Bit Sentinel team is involved in organising and supporting DefCamp, especially in its many challenges from the yearly Hacking Village and the largest CTFs from the region: D-CTF. Over 1,000 teams from 100+ countries join the online qualifications stage every year.
All this has brought us tremendous satisfaction! We’ve seen the community evolve, specialists become pros, and more and more students making their first steps in infosec.


European Cybersecurity Challenge
One of the things we most enjoy about our job is the opportunity to teach others what we’ve learned from both certifications programs and especially practice.
To do this, we’ve created a suite of dedicated training sessions and courses for security enthusiasts who want to learn the basics of information security.
What’s more, in 2019 we are the technical coordinator of one of the biggest CTF competitions in Europe: the European Cybersecurity Challenge.
This will be our second consecutive year of being actively involved in the ECSC. During the past years, we contributed to selecting the national team, trained them and helped choose the 10 participants that went on to participate in the ECSC.
In 2019, the ECSC will be held in Bucharest, at Romania’s Palace of the Parliament, one of the biggest buildings in the world. Teams from 19 participating countries will compete in the challenge.
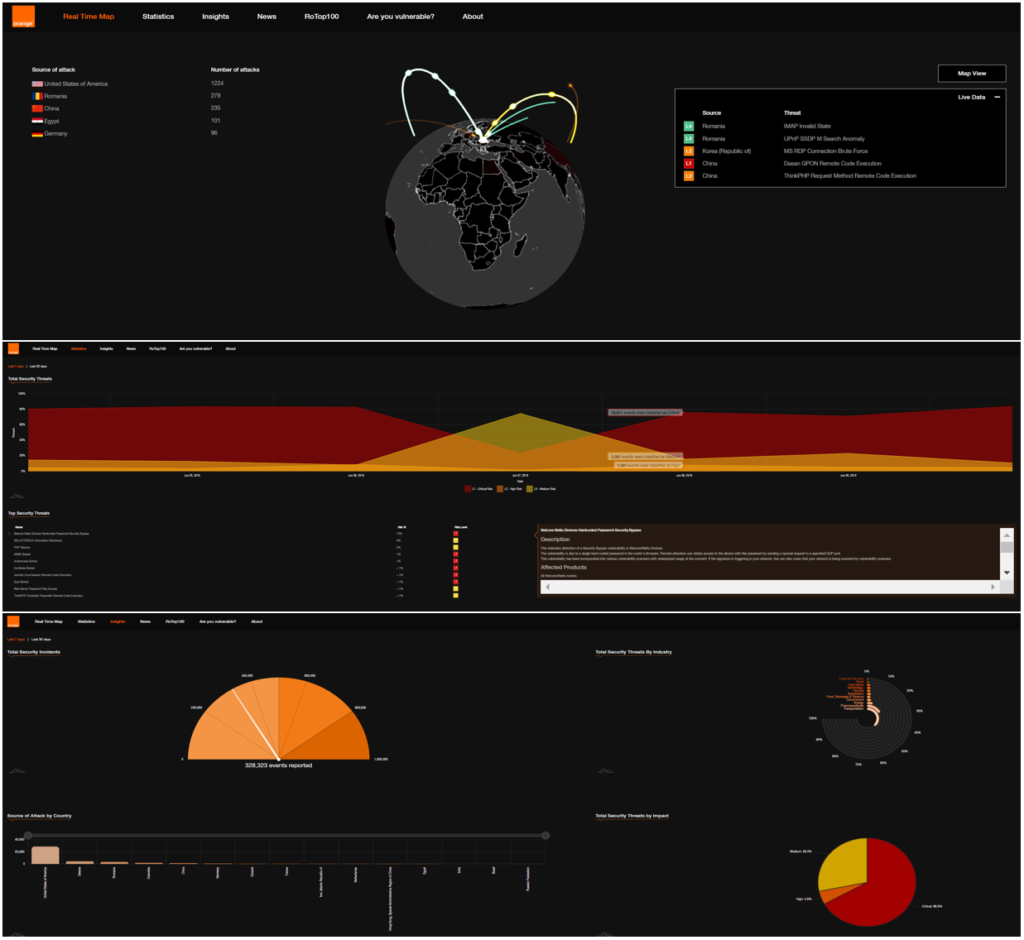
Orange BIS Threat Map
Our team worked together with Orange Romania to create the Orange Threat Map. Its objective is to present a high-level, visual perspective of the data collected by Orange Romania Business Internet Security agents deployed across Romania.
The map is a constant reminder of the scale of the challenge in cybersecurity, that’s also accompanied by extreme diversity and complexity.
Here’s the role the Bit Sentinel team played in building this awareness-oriented tool for businesses.
“I approached Bit Sentinel a couple of years ago when we needed a trustworthy cybersecurity partner with whom to develop BIS Threat Map. The team coordinated by Andrei proved to be very efficient and flexible in our collaboration.”, shared Cristian Patachia, Development & Innovation Manager, Orange Romania.
Customer stories_
Founded & led by Andrei Avădănei, one of the most respected infosec professionals in Romania and the CEE, Bit Sentinel works with customers from all over the world.
Our team personally oversees engagements and handles all inquiries, ensuring you get the biggest ROI for your investment.
Our customers refer to their experience of working with as “professional and very transparent” and “clear and responsive”.
We’d love to talk to you about your security needs and challenges!