Security researchers have discovered in February a critical vulnerability in multiple versions of Fortinet FortiOS and FortiProxy software allowing attackers to exploit this vulnerability by sending specially designed requests to the system, which could potentially enable them to run unauthorized code or commands on the affected system.
Bit Sentinel specialists analysed the Proof of Concept and published a Nuclei Template to integrate with your existing pipeline the discovery of Fortinet devices that are potentially affected.
About CVE-2024-21762
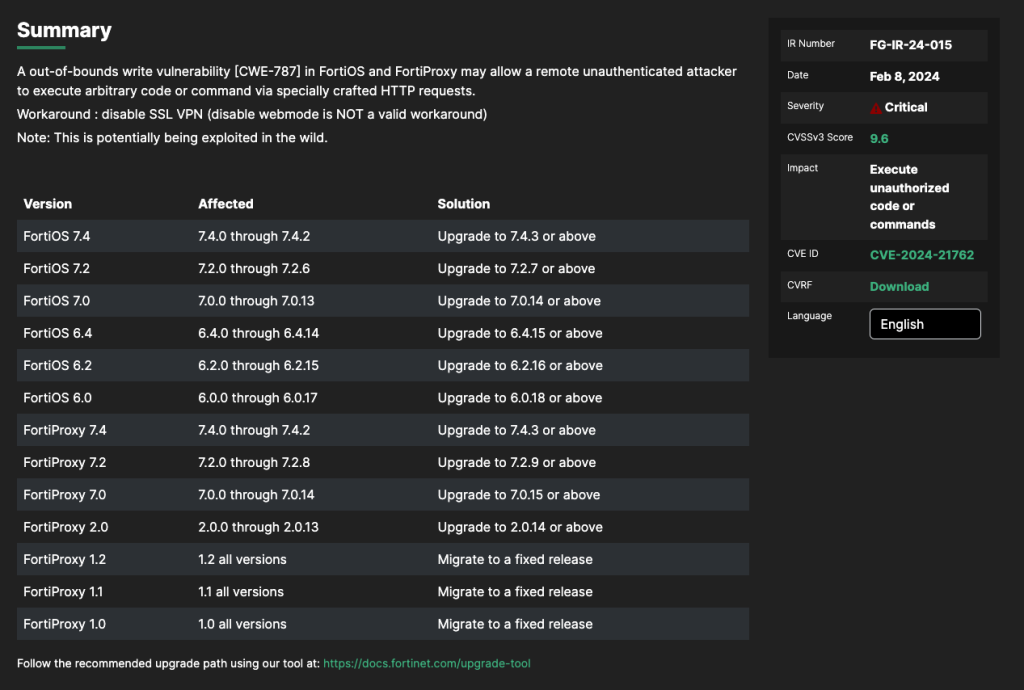
The CVE-2024-21762 exploit a vulnerability known as an “out-of-bounds write” error, which occurs when data is written outside the boundaries of allocated memory. It affects a range of software versions, including FortiOS versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.6, 7.0.0 through 7.0.13, 6.4.0 through 6.4.14, 6.2.0 through 6.2.15, 6.0.0 through 6.0.17, FortiProxy versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.8, 7.0.0 through 7.0.14, 2.0.0 through 2.0.13, 1.2.0 through 1.2.13, 1.1.0 through 1.1.6, 1.0.0 through 1.0.7.
Fortinet published an advisory on February 8th, identified by FG-IR-24-015, about the vulnerability and a workaround that by disabling SSL VPN, the risk is removed. The vulnerability is classified as Critical, having a CVSS v3 score of 9.6.
Shortly after the announcement, a security company published a Proof of Concept scanner about how to safely detect FortiGate SSL VPN is vulnerable to CVE-2024-21762 and other security researchers analysed the vulnerability.
According to another research published in March, this vulnerability bears resemblance to last year’s heap overflow issue linked to XOR operations (CVE-2023-27997), with both appearing to be innocent overflow flaws at first glance. Exploiting them involves complex techniques akin to those found in Capture The Flag (CTF) challenges.
However, compared with traditional CTF problems that attack heap managers, real vulnerabilities require more context structures and code logic to be exploited.
How to check if your FortiGate SSL VPN is vulnerable to CVE-2024-21762 using Nuclei Template
For those who don’t know, Nuclei is an Open Source vulnerability scanner backed by a strong community and enables the sending of requests to multiple targets using templates written in YAML, ensuring no false positives while allowing rapid scanning across numerous hosts. It supports scanning across various protocols such as TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, and Code, among others. Thanks to its robust and adaptable templating system, Nuclei is capable of facilitating a wide range of security assessments.
If you don’t have nuclei already, check their github repository. In order to verify if your FortiGate SSL VPN is vulnerable to CVE-2024-21762 using Nuclei Template you just need to:
CVE-2024-21762 Nuclei Template
Save the following in a file called “cve-2024-21762-check.yaml”.
id: cve-2024-21762-check info: name: Fortinet SSL VPN Out-of-bounds Write Vulnerability Check (CVE-2024-21762) author: LucianNitescu severity: Critical description: | A out-of-bounds write in Fortinet FortiOS versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.6, 7.0.0 through 7.0.13, 6.4.0 through 6.4.14, 6.2.0 through 6.2.15, 6.0.0 through 6.0.17, FortiProxy versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.8, 7.0.0 through 7.0.14, 2.0.0 through 2.0.13, 1.2.0 through 1.2.13, 1.1.0 through 1.1.6, 1.0.0 through 1.0.7 allows attacker to execute unauthorized code or commands via specifically crafted requests. reference: - https://bit-sentinel.com/cve-2024-21762-nuclei-template-for-scanning-fortigate-firewalls/ - https://fortiguard.com/psirt/FG-IR-24-015 - https://nvd.nist.gov/vuln/detail/CVE-2024-21762 - https://github.com/BishopFox/cve-2024-21762-check classification: cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H cvss-score: 9.8 cve-id: CVE-2024-21762 cwe-id: CWE-787 metadata: verified: true max-request: 1 vendor: fortinet product: fortinac shodan-query: title:"FortiNAC" tags: cve,cve2024,fortinet,vpn flow: http(1) && code(1) requests: - raw: - |+ POST /remote/VULNCHECK HTTP/1.1 Host: {{Hostname}} Transfer-Encoding: chunked 0 matchers-condition: and matchers: - type: word part: body words: - <script type='text/javascript' src='/remote/fgt_lang?lang= internal: true - type: status status: - 403 internal: true code: - engine: - py - python3 source: | import socket, ssl, os context = ssl.SSLContext(ssl.PROTOCOL_TLS_CLIENT) context.check_hostname=False context.verify_mode=ssl.CERT_NONE # credits: https://github.com/BishopFox/cve-2024-21762-check TIMEOUT=5 def send_req(host, req): try: s=socket.create_connection(host, timeout=5) except: return -1 ss=context.wrap_socket(s) ss.send(req) try: return ss.read(2048) except socket.timeout: return 0 check_req="""POST /remote/VULNCHECK HTTP/1.1\r Host: {}\r Transfer-Encoding: chunked\r \r 0000000000000000FF\r \r """ def check(host): baseurl="https://{}:{}".format(*host) r2=send_req(host, check_req.format(baseurl).encode()) if r2==0: return "Vulnerable" else: return "Patched" if __name__=="__main__": try: host=os.getenv('Hostname').split(':')[0] port=int(os.getenv('Hostname').split(':')[1]) except: print("fail...") exit() HOST=(host,port) print(check(HOST)) matchers-condition: and matchers: - type: word words: - "Vulnerable" # digest: 4a0a0047304502206cb27444814ca64ff154968dd36aec984699eb389050f90c8d010d9a2db81a7b0221009c4ca196b0ebc11dcbd86f45d4b08e6e0cfa1b4d72cbc3351155a6e468705cf4:4064d050bf4d41a5982c74d68fec3354Run the following command:
cat targets.txt | nuclei -t cve-2024-21762-check.yaml -code
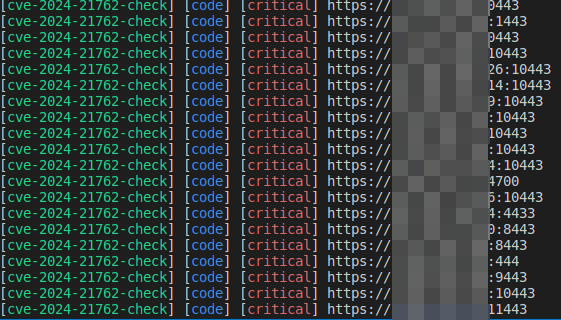
Below is an example of results obtained while scanning Bug Bounty targets: