“[Insert any company name here] tells customers their data was stolen during last month’s cyber attack”.
“The cyber attack on [insert any company name here] leads to $200M loss in revenue”.
“Cyber attacks from [insert any cyber criminal organization name here] now target this country’s critical infrastructures”.
Surely, you’ve read a lot of such titles lately, or any other variation on such subjects. You’ve most likely heard of a lot of cyber attacks happening lately and the devastating impact they can have. But how do cyber criminals actually do it? What does the behind-the-scenes work look like? To be more specific, have you ever wondered how cybercriminals develop and use highly complex malicious applications to hijack organizations and take profits?
As you might expect, the possibilities are endless.
For this article, we’ll go for a dangerous method cybercriminals use. We will talk about rootkits, share our thoughts on some examples of such programs – with a focus on the latest rootkit developed exclusively for the Linux Operating System, the Lightning Framework -, how they are developed by cybercriminals and how these programs can alter the entire security system of an organization.
What is a rootkit?
A malicious act that has the intention of destroying data, stealing data, or disrupting digital life in general is referred to as a cyber or cybersecurity threat. What is more important to remember is that both physical and digital types of malicious acts constitute threats. Cyber attacks may result in a wide variety of risks, including computer viruses, rootkits, data breaches, and Denial of Service (DoS) assaults, and the list goes on.
The term rootkit refers to a malicious software code that gives bad actors “root” access to an endpoint device. This is done by crossing the user privilege system in order to eventually reach the kernel or core, while obscuring the malicious code to prevent discovery.
There are two distinct components that make up the term rootkit:
- The particle “root” may be traced back to its roots in UNIX and other operating systems that are based on UNIX. In these types of settings, the term “root” refers to an account that has administrative capabilities. Whoever has access at the root level of the system can pretty much do anything they want with it. Because the ability to have unrestricted privileges can be dangerous in the hands of a bad actor, or even just a beginner, the root account is disabled by default in most modern UNIX-based operating systems like MacOS, Red Hat, and Ubuntu, and regular user accounts are issued instead. This is done to protect the system from potential threats. A standard user account will only have access to the bare essentials in terms of rights.
- The term “toolkit” was originally shortened to “kit,” which is where the “kit” in “rootkit” comes from. The malicious software developers’ toolkit is often made up of a variety of different bits of code, including scripts, programs, and other coding snippets.
Consequently, a rootkit is a malicious toolkit that is used to achieve privileged access while also establishing stealth and persistence.
In spite of its association with UNIX in the past, the word “rootkit” is now often employed in the realm of Windows. Windows-based operating systems are used to create the vast majority of the rootkits that are now in circulation.
Top 3 types of rootkits
Cybercriminals use a variety of rootkits – here are some examples:
1. Hardware or firmware rootkit
This kind of rootkit derives its name from the location on your computer where it is installed. The hard drive of your computer or the system BIOS, the software that is placed on a little memory chip that is located on the motherboard of your computer- each of these might get infected with this sort of malicious software. It’s even possible for the rootkit to infect your router. Rootkits like this allow hackers to read and intercept data as it is written to the disk.
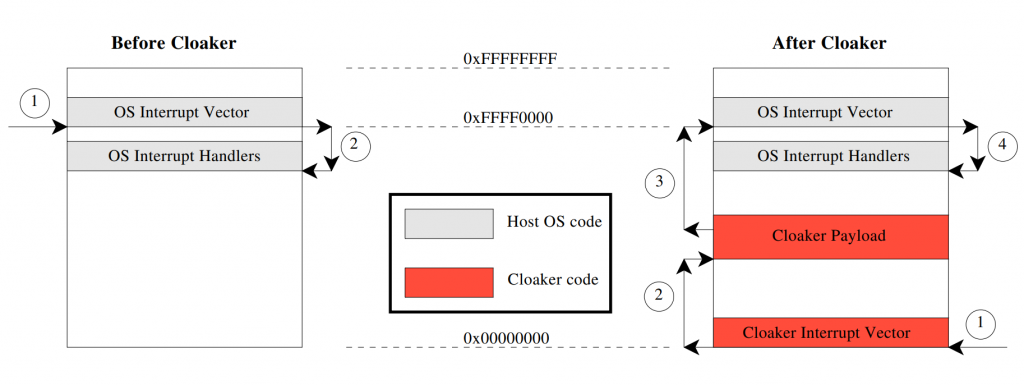
An example of such a malicious software is the Cloaker rootkit which is able to conceal itself from detection methods that are presently in use by using two particular hardware capabilities that are unique to ARM processors.
Cloaker operation is accomplished by the interception of interrupts. The original system and the typical flow of control during an interrupt are shown on the virtual memory map on the left. The diagram on the right displays the altered control flow that results from the installation of Cloaker.
2. Bootloader rootkit
The bootloader on your computer is an essential piece of software. When you switch on the machine, the operating system of your personal computer is loaded onto it. This system is then compromised by a bootloader toolkit, which causes the bootloader on your machine to be replaced with a compromised version. This implies that the rootkit gets active on your machine before the operating system has even had a chance to load.
An example of such rootkit is Olmasco, which is also known by the names SST and MaxSS. Olmasco is a member of the TDL4 bootkit family. We have been aware of this particular form of the family since the summer of 2011, when it was first discovered.
The most recent version of the Olmasco dropper includes protection against memory dumps and comes pre-packaged with a variety of strategies that may be used to prevent having one’s code examined by sandboxes. Unpacking is a key element of the dropper process, which begins after the dropper has been executed and continues throughout the unpacking step. During this stage, the dropper removes certain information from the portable execution (PE) headers. As a direct consequence of this, the PE headers in the unpacked code are spotless when the dropper gains control at the OEP (original entry point).
3. Kernel mode rootkits
These rootkits aim to compromise the fundamental components of the operating system on your machine. These vulnerabilities may be exploited by cybercriminals to alter the behavior of your operating system. Simply adding in their own custom code is all that is required of them. Because of this, they may have simple access to your computer and it will be much simpler for them to steal your personal information.
One of the rootkits that sees the most action in the wild is called Fu, and it’s one of the best. Other types of malicious software, such as variants of rbot and sdbot, have made use of its features in order to hide themselves in the past. Fu is a rootkit that operates in kernel mode and functions by making modifications to the data structures of the kernel. Because of this, it is able to keep things such as procedures a secret.
Technical analysis of the latest Linux rootkit discovered
On the 21st of July 2022, security researchers working for Intezer uncovered a sophisticated malicious program developed by hackers. It is dubbed Lightning Framework and it is designed to attack Linux operating systems.
Because it cannot be detected and because it has the ability to install rootkits on the machine that it is targeting, the Framework poses a significant threat.
On infiltrated Linux machines, Lightning Framework will download and install all of the malware’s other modules and plugins, including its core module. This is accomplished via the use of a downloader component that is developed using a straightforward construction method.
In order to avoid detection on infected PCs, the virus makes use of a tactic known as typosquatting and will disguise itself as the Seahorse GNOME password and encryption key manager.
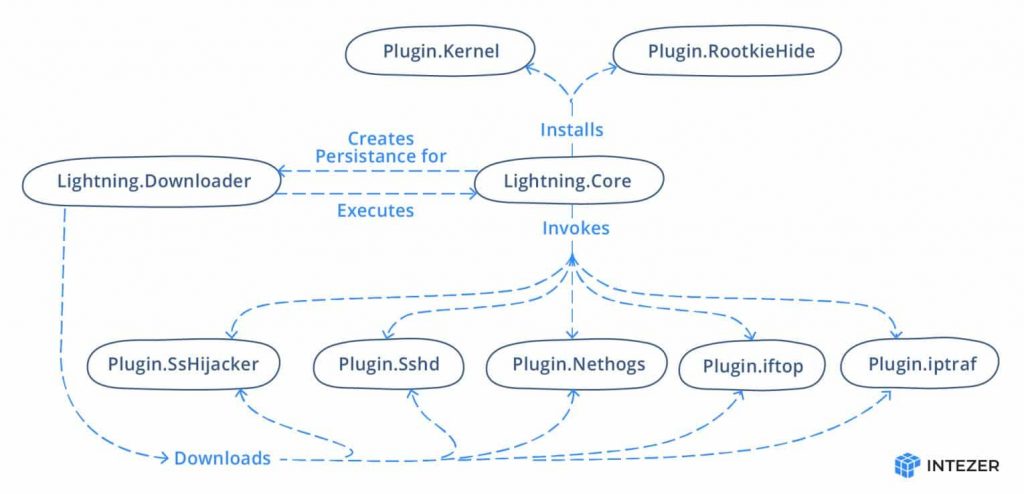
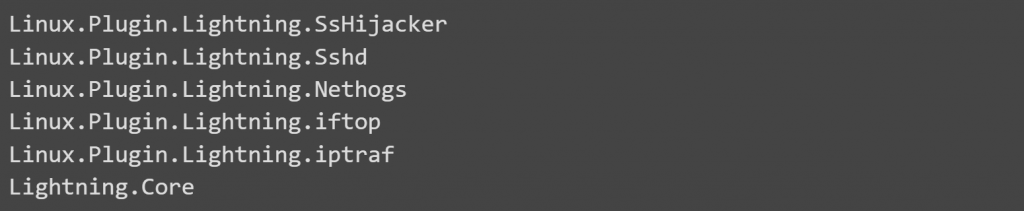
The major components of the framework are a downloader, a core module, and a range of plugins. In addition, the framework provides a host of other add-ons. The malicious program utilizes open-source software in the form of plugins in order to further its own ends.
The following figure, created by Intezer malware analysts, illustrates the framework’s underlying organizational structure:
The core module’s execution and the retrieval of the other modules’ components are the primary responsibilities of the downloader module. In order for the framework to stay undiscovered, it relies heavily on a combination of typo-squatting and masquerading.
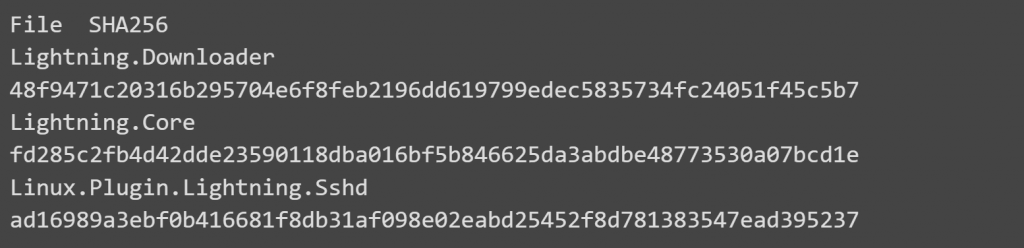
Lightning.Downloader
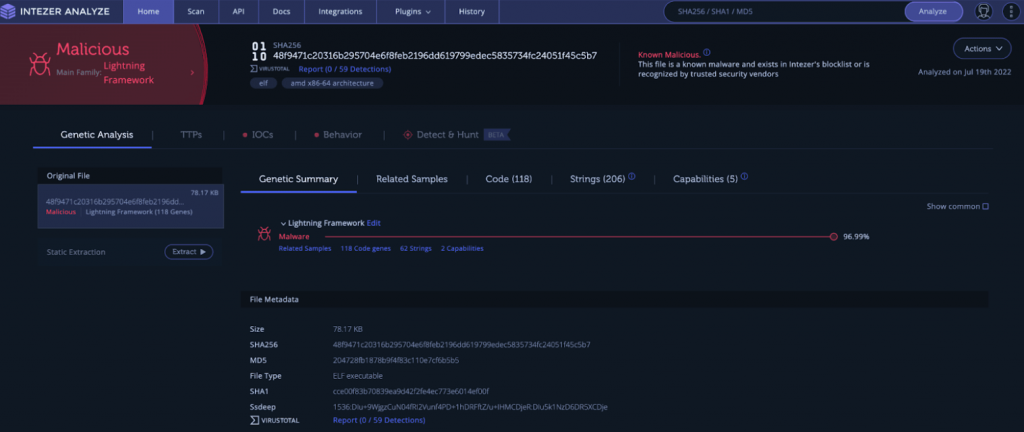
Since Intezer indicates that the downloader module is situated in the working directory /usr/lib64/seahorses/, having the name kbioset, a person doing a cursory investigation may conclude that the directory is associated with the password and key management program seahorse. The command and control server will get a GUID that was generated by the downloader using the host name and network adapters as fingerprints. This GUID will be transferred to the C2 server. Then the C2 server will get and install the following plugins on the targeted system:
In the picture below we can see more details regarding the alert triggered by the malicious downloader in the Interzer Analyzer tool.
Lightning.Core
The core module’s responsibilities include the configuration of the persistent system.
It does this by generating a script that is run every time the operating system starts up.
An apparent effort to typosquat elasticsearch is made by first generating a file that is placed at /etc/rc.d/init.d/elastisearch. This is the initial step in the boot execution process.
As presented by the Intezer cybersecurity specialists, the elastisearch file has the following content:

The malicious software also implements a method known as timestomping, which modifies the timestamp of the script such that it coincides with the timestamp of one of the fundamental Linux files. In such a way that, if an investigator doesn’t look into it further, they may assume that it was made when the system was first being set up.
A rootkit is also used by the framework in order to conceal its Process ID (PID) and any network ports that are associated with it. Any reference to files that are currently operating in the framework may be removed by the rootkit.
This table offers useful information to the public about how the Lightning Framework plugins work.
| Lightning.Downloader | kbioset | The persistent module that downloads the core module and its plugins |
| Lightning.Core | kkdmflush | The main module of the Lightning Framework |
| Linux.Plugin.Lightning.SsHijacker | soss | There is a reference to this module but no sample found in the wild yet. |
| Linux.Plugin.Lightning.Sshd | sshod | OpenSSH with hardcoded private and host keys |
| Linux.Plugin.Lightning.Nethogs | nethoogs | There is a reference to this module but no sample found in the wild yet. Presumably the software Nethogs |
| Linux.Plugin.Lightning.iftop | iftoop | There is a reference to this module but no sample found in the wild yet. Presumably the software iftop |
| Linux.Plugin.Lightning.iptraf | iptraof | There is a reference to this module but no sample found in the wild yet. Presumably the software IPTraf |
| Linux.Plugin.RootkieHide | libsystemd.so.2 | There is a reference to this module but no sample found in the wild yet. LD_PRELOAD Rootkit |
| Linux.Plugin.Kernel | elastisearch.ko | There is a reference to this module but no sample found in the wild yet. LKM Rootkit |
The most important part of the structure is this fundamental module, which goes by the name kkdmflush. It is the module that the malicious software uses in order to carry out the execution of its plugins and take commands from its C2 server.
This piece of malware will also install its very own backdoor that is based on SSH by starting an SSH server by making use of one of the plugins that were downloaded. This brings us to the very end of this list (Linux.Plugin.Lightning.Sshd).
The core module has the following commands:
| SystemInfo | Fingerprints the machine |
| PureShellCommand | Runs Shell command |
| RunShellPure | Starts the Linux.Plugin.Lightning.Sshd (SSH Daemon) plugin |
| CloseShellPure | Terminates the Linux.Plugin.Lightning.Sshd plugin |
| Disconnect | Exits the Core module |
| GetRemotePathInfo | Collects the summary of given path |
| KeepAlive | No action, connection remains alive |
| UploadFileHeader | Checks access of file |
| FileEdit | Gets contents of file and time meta |
| TryPassSSH | Adds a public key to the root/.ssh/authorized_keys file |
| DeleteVecFile | Deletes the specified file or path |
| PreDownloadFile | Calculates a checksum of the file |
| DownloadFile | Sends a file to the C2 |
| DeleteGuid | Removes the framework |
| UpdateVersion | Calls the Downloader module to update the framework |
| UpdateRemoteVersion | Updates the framework including the downloader |
| Socks5 | Sets up a Socks5 proxy |
| RestorePlug | The same as UpdateVersion |
| GetDomainSetting | Fetches the contents of the malleable C2 configuration file (cpc) |
| SetDomainSetting | Updates the contents of the malleable C2 configuration file (cpc) |
| InstallKernelHide | Fetches the OS release |
| RemoveKernelHide | Removes kernel module |
| UpdateKernelVersion | Removes the kernel module and runs uname -r |
| OverrideFile | Overwrites specified file |
| UploadFileContent | Writes data sent from server to file |
| LocalPluginRequest | Either write the LD_PRELOAD rootkit or LKM rootkit |
Network Communication
TCP sockets are used by the Core and Downloader modules to talk to each other over the network. Using JSON, the data is put together. For each new building, the C2 data is stored in a polymorphic encoded configuration file. So, hashes won’t be able to find configuration files anymore. The key is at the beginning of the file that has been encoded.
The decoded configuration is put together with the help of JSON. In the sample that was looked at, the IP address is 10.2.22.67 and the port is 33229.
If the actor uses the RunShellPure command, there is a way to communicate without the actor doing anything. On the Linux-infected computer, the SSH service is turned on.
Plugin.Lightning. Add-on to Sshd. With the private and host keys that are hardcoded into the plugin, an attacker could use SSH to get into the system and use the OpenSSH daemon to install their own backdoor.
The complete technical analysis can be found on the Intezer blog and here.
We know, there’s a lot of technical talk around rootkits. In the end, everything comes down to this question:
Why are rootkits dangerous for companies?
If you don’t regularly scan your computer for rootkits, you’re at risk of being infected. These hideous predators are a good representation of what it means to be a true parasite. These criminals are damaging your computer in a secret manner. Consequently, we find it important to understand how rootkits work and how to avoid them.
Cyber espionage operations, attacks aimed at stealing money, and plans to utterly destroy the infrastructure of the company they are meant to enter are all methods that use rootkits.
- Rootkits pose a great danger due to their high degree of efficiency, even though their goals aren’t new. The ability to take control of other organizations’ systems without their awareness has resulted in irreversible consequences.
- A rootkit makes it easier for hackers to infiltrate and take over a computer system, eavesdrop on its activities, steal data, and launch malware and other malicious attacks. If you receive phishing emails, install programs, or visit hacked websites, “silent guests” may show up on your computer.
- A rootkit may be hidden by another piece of software. This means it might go unnoticed for a long time. You may not be able to undo the damage that has already been done. A computer’s performance might suffer, as could a company’s productivity.
- This kind of malware may also get access to a company’s network and the personal information of its consumers. It specifically targets the device’s administrator level of access. What makes a rootkit cyberattack dangerous is what happens in the wake of it. There’s a good chance that your consumers will lose faith in you when your computer’s sensitive information is compromised by a hacker at this level.
- You can eavesdrop and gather passwords using rootkits, but they may also be used to install other applications.
Examples of rootkits attacks
Threat analysts who have been watching the activities of LightBasin, a financially driven gang of hackers, reveal the finding of a previously undisclosed Unix rootkit that may be used to steal banking information from ATMs and execute fraudulent transactions.
LightBasin, also known as UNC1945, has been documented as being active as far back as the year 2016, and it is believed they have been successful in breaching the security of thirteen different telecommunications companies all over the world by utilizing bespoke tools in conjunction with their extensive knowledge of telecommunications protocols.
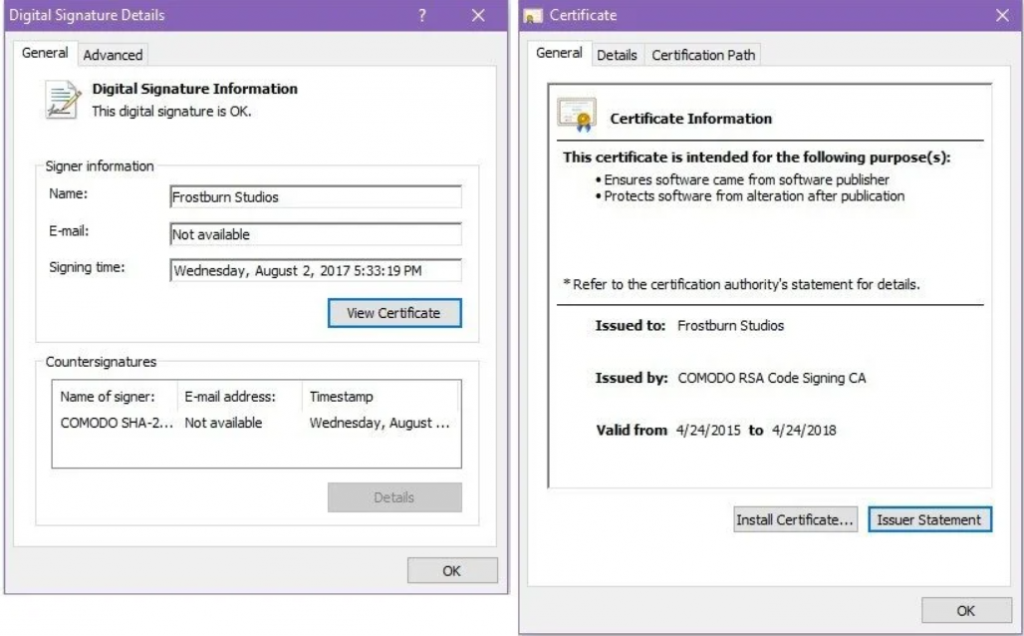
A Chinese hacker outfit employs a brand-new Windows rootkit called “Fire Chili.”
A recent campaign using the Log4Shell vulnerability to deliver a unique rootkit called ‘Fire Chili’ was discovered by Fortinet to have been carried out by the Chinese advanced persistent threat organization known as Deep Panda. This operation targeted VMware Horizon servers.
When the assaults are carried out, the rootkit is digitally signed by legitimate certificates, which enables the possibility to evade detection by security tools and load into Windows without triggering any alerts.
Recommendations on how to keep rootkits at bay
It is critical that your workers’ personal devices are optimized in order to keep rootkits out. There are several approaches to improve cybersecurity. Rootkit scanners (A) and even preemptive blocking (B) may be part of the solution.
(A) Detecting rootkits, as the name indicates, is the primary goal of rootkit scanners. For rootkit detection at different levels of your network, it may be required to use several scanners.
Scanners have the potential to find dangerous programs on your computer. To rid your system of a rootkit, you may need to wipe your hard drive clean or perhaps buy a new hard drive completely. Reinstalling your operating system may be essential from time to time.
Taking a backup of your data and following the recommended procedures are your only options since rootkits may be difficult to remove after they have been identified.
(B) In addition to scanning the system, preemptive blocking may also be used as a preventive measure. Training your staff to avoid clicking or opening strange links and advertisements, like phishing schemes, is an example of this.
Keeping up with the latest software updates, scanning networks, and running anti-virus may also be helpful in preventing security breaches.
To prevent malware from being downloaded to your computer without your knowledge, a technique known as “drive-by downloads” is used. Malicious code may be injected into legitimate sites, causing them to launch malware downloads when a user accesses them. To guard against this, make sure that your operating system, web browsers, and other apps are all up to date and patched with the most recent safeguards available.
Links or attachments supplied from unknown sources might lead to a drive-by download if clicked on. The best course of action is to promptly delete any unwanted email from an unknown source. If the sender is recognized but the email is unsolicited, establish contact with the sender to double-check.
Conclusion
We can’t stress this enough: don’t be fooled into thinking that your computer won’t be targeted by hackers because it isn’t significant enough.
For starters, your PC is involved in financial activities. You may potentially be accessing your company’s resources using your own computer. In the event of a successful hacking attempt, unethical hackers may be able to get access to the network of your company via your PC. In addition to your financial information, your computer may also include personal information about you.
Because of the private information stored on them, every PC is a potential target. The sooner you take the necessary measures to safeguard your information (this includes constant research as well), the better you’ll build up your cyber resilience!
About the Author

Valentina Galea
Valentina works as Ethical Hacker at Bit Sentinel. She has extensive expertise in mobile security and forensics and is currently exploring the subject of threat hunting. She discovered her passion for cybersecurity 5 years ago and she continues to develop her skills as much as she can in this field.
In the past, Valentina has proposed exercises for ECSC 2020, UNbreakable Romania 2020 and DefCamp Capture the Flag 2020.