As your employees work from their own homes, sometimes using their own devices, you might be worried about how they handle your company’s data and confidential assets.
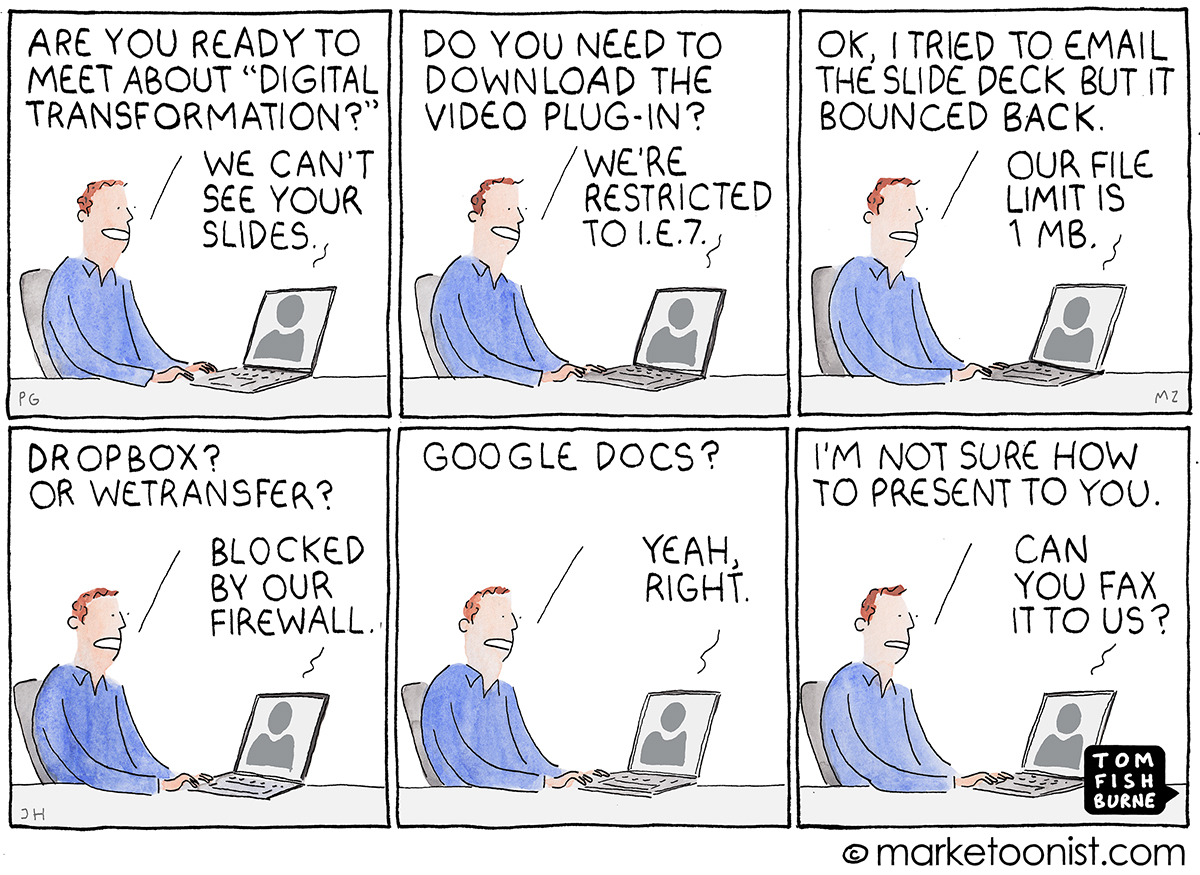
Are they sharing important documents using Wetransfer?
Are they chatting on Whatsapp?
Are they using their company phones to click on Instagram ads?
If you’re wondering what they might be doing, start from your own habits. If you’re doing all these things, most likely so are they.
When trying to stay productive and get work done, employees will find the tools they need. Their intentions are good. While you roll out new company policies and solutions, your team must keep going.
The findings of a 2018 survey of over 1,000 ‘non-desk’ employees in 5 countries is a good reality check for business owners who care about business continuity and the role security plays in it:
- 64% use their mobile devices for work-related communications
- 1 in 5 workers “use messaging apps such as WhatsApp, Facebook Messenger, Skype, or Telegram as the primary channel to communicate with fellow colleagues, managers, and the head office”
- 53% use messaging apps for work-related matters between one and 6 times/day
- 16% of them said their HR or internal communications departments are not aware of this usage.
- 27% “said their biggest frustration […] is the lack of collaboration and sharing of relevant company or product information, and learnings with their fellow colleagues, teams, office staff, and management.”
These numbers are probably much higher in all companies around the world right now. Collaboration and information sharing are crucial for getting work done and, if the company-issues devices and apps don’t support them, employees will find workarounds.
Every company has a BYOD security issue right now
Before the pandemic, many companies, no matter their size, allowed contractors, partners, customers, and suppliers to access corporate data on their personal devices. Knowingly or not, now every organization in the world does, yours included.
The problem is all these unmonitored and often poorly secured devices give cybercriminals more options to roll out their malicious tactics.
For example, the Bitglass 2018 BYOD Report highlights that 43% of firms don’t know if devices accessing corporate data have downloaded malware.
What’s more, companies are worried about BYOD security issues such as data leakage (61%), unauthorized data access (53%), and the inability to control uploads and downloads (53%).
The threats match this surge in BYOD. In their 2018 Internet Security Threat Report, Symantec mentioned they blocked an average of 24,000 malicious mobile applications each day!
It’s no surprise that Deutsche Bank banned the use of SMS, WhatsApp, and other messenger services as of January 2017 based on rigorous compliance conditions banks must follow.And let’s not forget the EU GDPR and the impact it has on BYOD and using unapproved software to handle company and customer data.
Case in point, last October, a hefty GDPR fine hit one of the largest banks in Romania:
“Romania’s National Supervisory Authority for Personal Data Processing (ANSPDCP) has fined Raiffeisen Bank and local online credit platform Vreau Credit with a total amount of EUR 170,000, out of which EUR 150,000 to be paid by Raiffeisen, for a broad range of data confidentiality breaches.
More exactly, Raiffeisen Bank Romania carried scoring assessments based on personal data of people who registered on the Vreau Credit platform, supplied through WhatsApp by the platform’s employees, and then returned the outcome to Vreau Credit using the same communication means.”
It may be tempting to blame the users for their behavior and choices, but let’s switch perspectives for just a minute.
How it looks like from the user’s side
“When I visited a company recently, a VP asked if I could help with a video-recording session in Camtasia, but first he had to install the software. He booted up his laptop, whose encrypted drive prompted him for a password. To get into Windows he had to put in his Active Directory username and password, which he told me requires updating every three months and has fairly high complexity requirements, so it’s hard to remember.
When he finally got into his laptop and began to install Camtasia, he was asked for the admin password. He didn’t have that password, so he had to call for IT to come and enter it.”
This story from the excellent article on the evergreen topic of security and usability is an important reminder of what the end user’s experience looks like. We can’t ignore that security layers make life difficult for employees – it’s why security gets a bad reputation.
A little empathy goes a long way in this complicated negotiation between security and usability. There are no perfect solutions or plans, no definitive answers. Like all important things, your company’s security – which is essential for your business continuity – is a matter of good decisions made on an ongoing basis.
Resistance to change – and control
There are two things that increase the frustration for your employees right now: the overwhelming change coming in from every angle (professional, personal, global) and the fact they work remotely without a proper setup for it.
As humans, we’re not wired for change, so there’s a natural resistance to it. What’s more, when the company imposes new security measures, they’re often seen as limitations, as means for control (which some organizations actually use them for, unfortunately).
The most extreme form is full control of a device, the “you can use it but we see everything you do” approach. From a risk perspective, this is the best option for companies. From the employee’s viewpoint, it’s the most frustrating – even infuriating – scenario.
So what is the solution?
Increased security is a key layer in your digital transformation strategy but it’s also deeply connected to every other part of the process.
The best solutions that work in the long-term are rooted in the employees’ needs and your company dynamic. They’re also based on mutual trust:
- the company trusting the employees to do their best work, as safely as they can
- the employees trusting the company deploys security measures to protect and not control them.
So what would this look like?
Here are a couple of aspects to consider when balancing security and usability to make remote work secure for all.
Balancing security and usability – essential questions
Start by asking yourself:
What are people used to?
What are they expecting?
Potential answers include:
- people are used to logging in with a username and password
- people are accustomed to easily recovering access to their account (the “forgot password” option part of the logging screen)
- it’s familiar for people to turn to a specialist when things get too difficult for them to fix (customer support agent, support ticket, etc.).
Ensuring a consistent approach across channels (username/password combo) and a single point of contact for support requests can make a huge difference in this hectic context!
Another question to ask is:
Do you employees know WHY you’re doing this?
Make sure you have a simplified version of your internal policies, the ones that keep you compliant with all sorts of regulations. Your employees may not understand legalese (and it may also bore them), so making these documents easy to read, access, and turn to when needed can help your team understand why security actions are necessary.
If you don’t have these policies yet or would like to improve them, you can always reach out to us for help and make the entire process faster and more effective.
14 tips for secure collaboration
To wrap up, we’d like to leave you with a bunch of tips on secure collaboration. These are ready and easy to apply, giving your employees a sense of control over their own security. Strengthen that with publicly expressed trust – and a bit of security training – and you’ll make more progress than most companies in your industry and beyond!
- Update the most commonly used browsers (if they don’t have auto-update, like Chrome does).
- Advise employees to check and delete unnecessary browser add-ons.
- Provide them with the option to install a security plugin for their browser (such as Malwarebytes, for example).
- Require them to set and use unique passwords across their company accounts and for other software they use for work.
- Provide them with a simple to use password manager they can also use to safely share passwords with other colleagues, if needed.
- Make sure you can remote wipe company owned devices to remove sensitive data if needed.
- Provide a list of examples of phishing attacks, online scams, fake news, and other cybercriminal tactics they might come across, so they can recognize these threats more easily.
- Give employees access to secure cloud-based file-sharing software to make collaboration easier.
- Provide your team with communication software that covers their needs, so they don’t have to user alternative channels, such as Whatsapp or Facebook Messenger.
- Make sure they can use cloud-based project or task management software to track their tasks, assign tasks to each other, and share progress.
- Ensure employees know how to use a VPN – and why.
- Give explicit guidance for backing up their work in case you don’t have an automatic setup for this.
- Schedule regular check-ins with your team. Listen to their feedback on workflows and try to create better work opportunities to keep everyone involved and in the loop about any changes or updates to policies.
- Have a key person employees can go to for advice when they feel unsure or when they want to report a potential threat. This is also essential for your incident response plan.


