Each time an emergency hits any sector – or society at large – cybercriminals pounce to exploit the situation.
Feeding off massive societal changes such as well developed internet infrastructure, an increase in online payments and social media usage, and corporate digital transformation, cybercriminal operations often take the form of organized crime.
Cybercrime now involves using botnets (networks of infected devices without the owners’ knowledge), backdoors that allow persistent access into companies’ infrastructures and devices, and sophisticated malware that can override traditional security controls.
Malicious actors also trade hacking expertise in online forums, use bulletproof hosting to distribute their attacks, and round up technical writers to create ever more compelling content to lure victims into clicking and opening links and attachments that belong in the spam folder.
This is not amateur hour. These well-funded cybercriminal operations focus not only on monetary gains but that sometimes reach further, as the European Parliament reports:
“[…] attacks on industrial control systems and networks aimed at destroying critical infrastructure and economic structures as well as destabilising societies, as was the case of the ‘WannaCry’ ransomware attack of May 2017, are also growing in number and impact […].”
In their Cyber Risk for the Financial Sector: A Framework for Quantitative Assessment, the International Monetary Fund also emphasized that:
“Cyber risk has emerged as a key threat to financial stability […].”
This concerns your company as much as any other organization out there.
The more familiar you become with online criminals’ methods, especially when they’re in land-grabbing mode, the better decisions you can make about your security. This involves not only choosing the right technology but also the right experts to work with and the right priorities to cover human behavior in your company – including your own.
When a crisis hits, expect these cyberattacks
Everything old is new again.
Cybercriminal tactics have evolved, but most attacks leverage the same types of vulnerabilities – both in technology and in the human mind and behavior. But while tactics may be familiar, the shapes they’re delivered in are not.
Highly motivated attackers have a lot of time – and sometimes a lot of resources – on their hands to find your most vulnerable points and ruthlessly pursue them. You need to cover all your bases and vulnerabilities. They only need to successfully exploit one of them.
1. Phishing and its many shapes
Long gone are the days when phishing emails were written in broken English, making them easier to single out and send to the spam folder.
Malicious actors have improved their tactics to emulate legitimate emails and interfaces from well-known companies that users trust so much as to override their usual mental checks:
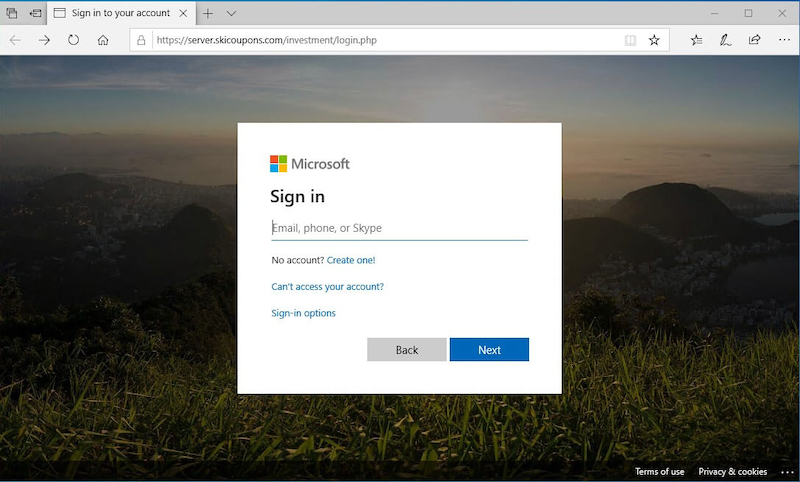
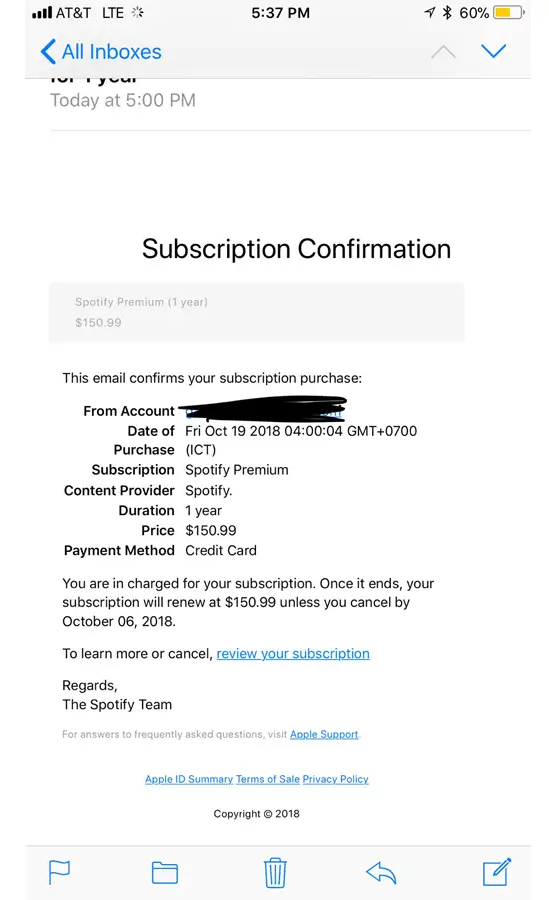
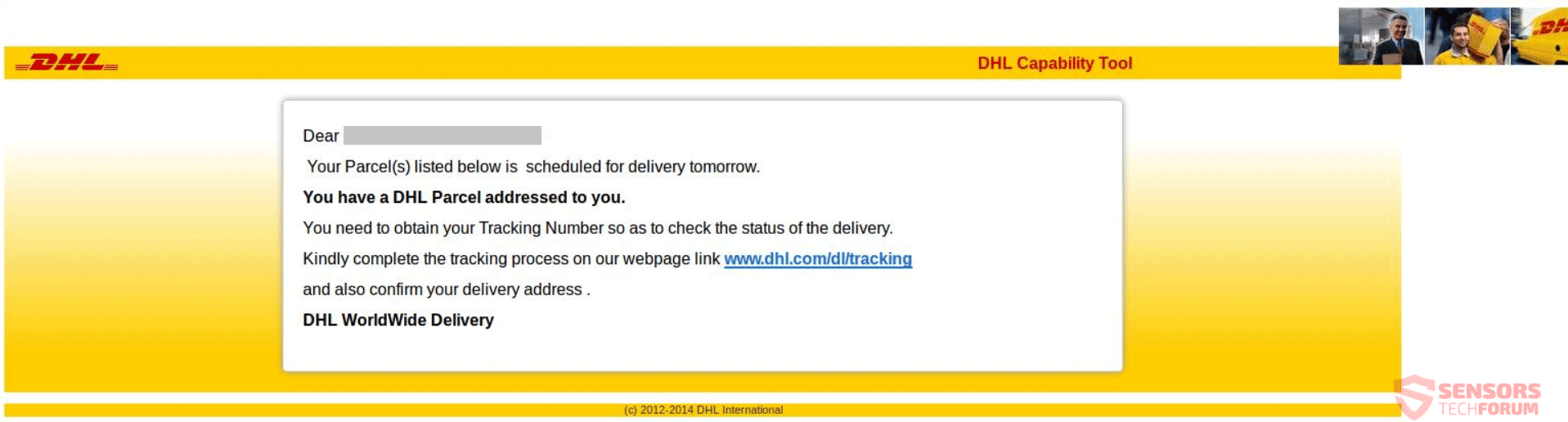
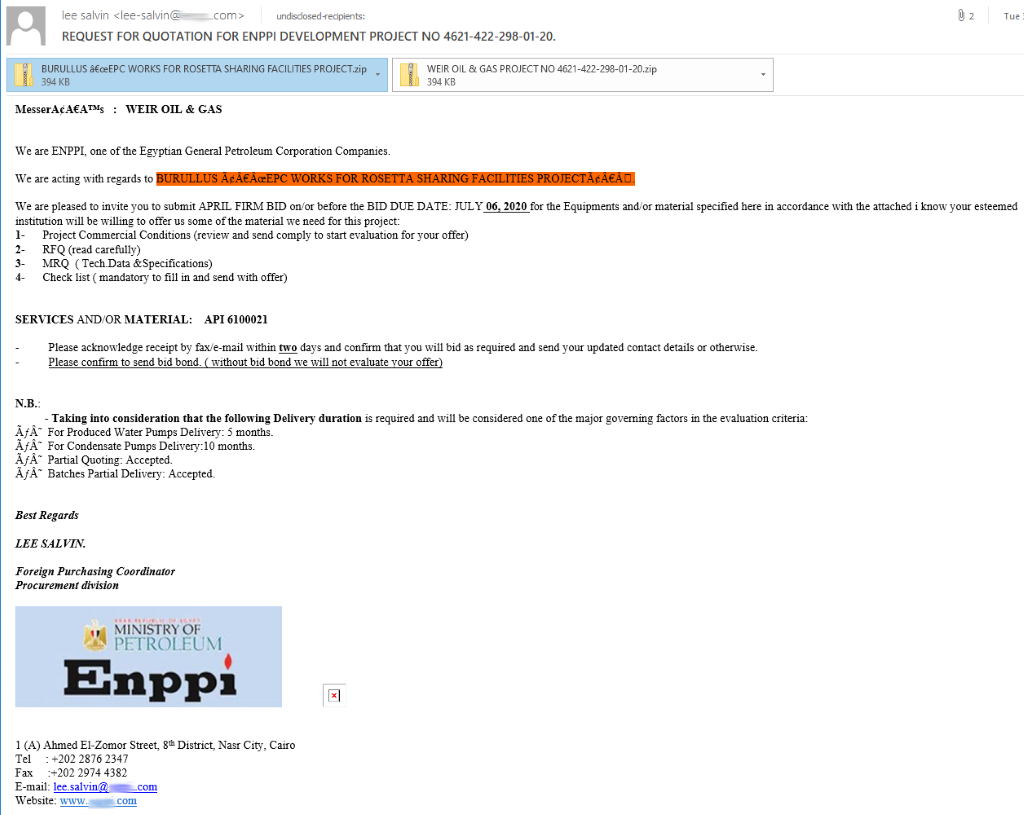
Impersonating brands is not the only thing online criminals have become undeniably good at. They’ve also improved their methods used for CEO fraud, smishing (SMS phishing) and vishing (voice phishing), whaling and clone phishing, or pharming.
There’s a huge variety in phishing attacks and no shortage of cunning tactics that share a common goal: to trick internet users to act against their better judgement.
The damage costs organizations billions of dollars and leads to bigger, company-wide problems. The data is extremely aggravating:
- 32% of confirmed data breaches involved phishing (source)
- 37.9% of untrained users fail phishing tests (source)
- 26 billion lost globally to business email compromise crimes between June 2016 and July 2019 (source) with over 1.7 billion in 2019 alone (source)
- Puerto Rico’s government lost $2.6 Million in a single phishing attack (source).
Each time a regional or global crisis erupts, malicious hackers jump at the opportunity! Contexts dominated by fear, uncertainty, and doubt (the FUD principle) make it easy for online criminals to disorient users by:
- Impersonating trusted brands and people
- Tempting users with too-good-to-be-true offers and promises
- Exploiting people’s eagerness to get the latest news and information
- Persuading them they’re on a tight deadline to act in an important matter, and more.
These triggers are evergreen because they use social engineering tactics to manipulate people’s psychology, which makes anyone and everyone susceptible to compromise.
2. Scams
From impersonating Hollywood stars to defraud people of thousands of dollars to in-game currency scams, to selling fake attendees lists for major music festivals, cybercriminals are as creative as you can imagine – actually, even more than that.
Major world events or even recurring ones – like music festivals – prompt quick response from online scammers, who seek to manipulate, exploit, and fleece people from all walks of life.
While phishing attacks can come via SMS, voice calls, tweets, pop-ups, or even calendar links, the same is true for scams. While they often seem more benign, scams are just as dangerous as phishing attacks.
Fake charities, rogue online shops, fake supermarket vouchers distributed via instant messages are a common occurrence. Besides deceiving people and getting their data and/or money, they can also be a tactic cybercriminals use to plant malicious software on the victims’ devices, opening up your company to further and more costly risks.
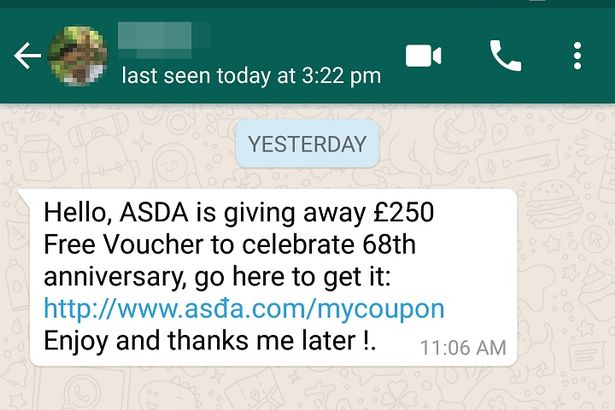
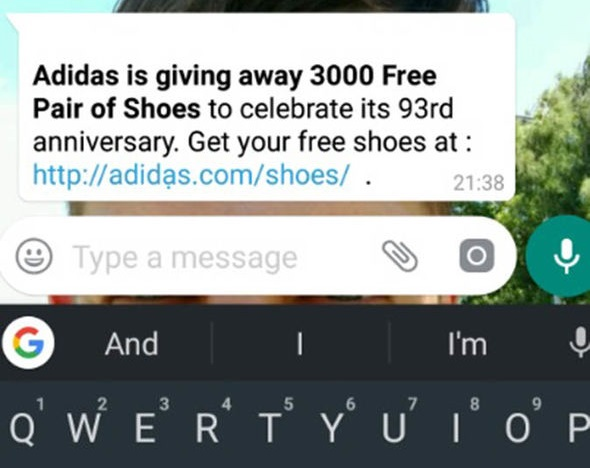
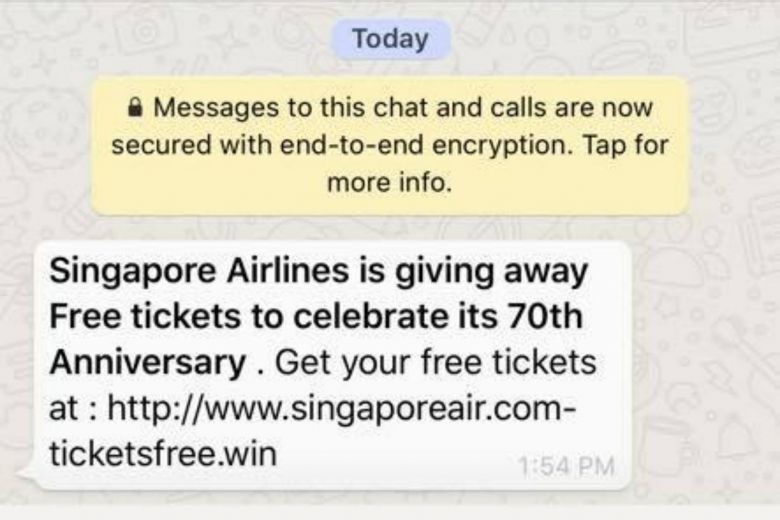
These examples are variations of the same scam, but many others can be seen in the wild.
When it comes to exploiting worldwide crises, we have a ton of timely examples to use as cautionary tales.
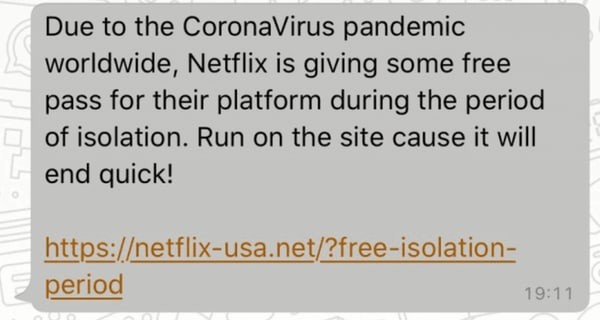
“In mid-March, as a number of countries were going into lockdown due to the coronavirus outbreak, German health authorities contracted two sales companies in Zurich and Hamburg to procure EUR 15 million worth of face masks. With a global shortage of medical supplies complicating usual business channels, the buyers followed new leads in the hopes of securing the masks.
It all started with an email address and website which appeared to be linked to a legitimate company in Spain selling face masks. Unbeknownst to the buyers, the site was a fake and their legitimate email addresses had been compromised.” (Source)
Every time something bad happens that triggers people to experience intense emotions (fear, doubt, pain, frustration, etc.), expect that online criminals will use these to launch more attacks and turn more people into victims – both in the short and the long-term.
3. Fake news
In uncertain times, people need something to believe in.
So they seek out information to cover the gaps in their know-how, often picking ideas and data that align with their view on life.
As humans, we’re also tempted to trust spontaneous opinions and messages more than we trust experts. This slippery slope is what malicious actors ferociously exploit.
As we mentioned in our in-depth guide on the influence of fake news on companies like yours, this malicious tactic can impact financial markets, causing stocks to drop.
“Metro Bank in the UK was forced to take to Twitter in May to reassure customers of its financial health after its share price dropped 11 per cent due to false rumours circulating on WhatsApp and Twitter, warning that the bank was close to collapse and encouraging customers to empty their accounts.”
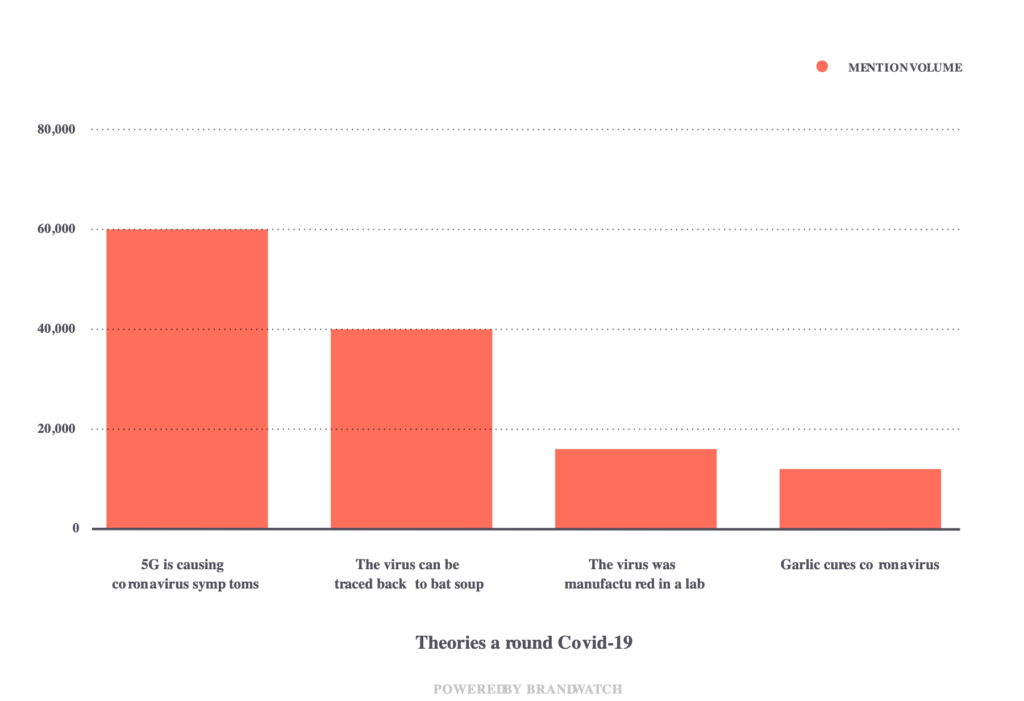
The Covid-19 pandemic has spurred unusual volumes of fake news and misinformation campaigns ranging from misrepresentation of real-life details (i.e. swans in some parts of Venice) to conspiracy theories whose origins remain unknown (i.e. 5G causing coronavirus symptoms).
Whatever form they come in, fake news is as dangerous to yourself as a business owner and decision-makers as they are for your family, friends, and society at large.
4. Mobile malware
The need for human connection and information surge in importance when a crisis hits. From family issues to global problems, we all tend to spend more time online, whether it’s exchanging messages via WhatsApp or Facebook or scrolling through Facebook and news sites.
That means we spent more time on our mobile devices – especially smartphones.
In their Q1 report for 2020, Facebook announced:
“For the first time ever, there are now more than 3 billion people actively using Facebook, Instagram, WhatsApp or Messenger each month. That includes 2.6 billion people using Facebook alone, and more than 2.3 billion people using at least one of our services every day.
In many of the places hardest hit by the virus, messaging volume has increased more than 50%, and voice and video calling have more than doubled across Messenger and WhatsApp.
In Italy, for example, we’ve seen up to 70% more time spent across our apps, Instagram and Facebook Live views doubled in one week, and we’ve also seen time in group video calling increase by more than 1,000% over March.”
“Between WhatsApp and Messenger, there are more than 700 million daily actives participating in calls. We’re doubling the size of WhatsApp video calls from 4 to 8.”
What that means for your business is more exposure – not just to web-based threats, but also to things like:
- user errors (e.g. tapping a suspicious ad or pop-up by mistake)
- user negligence (e.g. your employee’s kid get their hands on the phone and accidentally unlocks it – if it doesn’t have any sort of screen lock protection)
- a weaker ability to spot phishing attempts because users can’t see the full URL, as they do on desktop, and the list could go on.
Because of these aspects and others, cybercriminals have increased their attacks targeting smartphones.
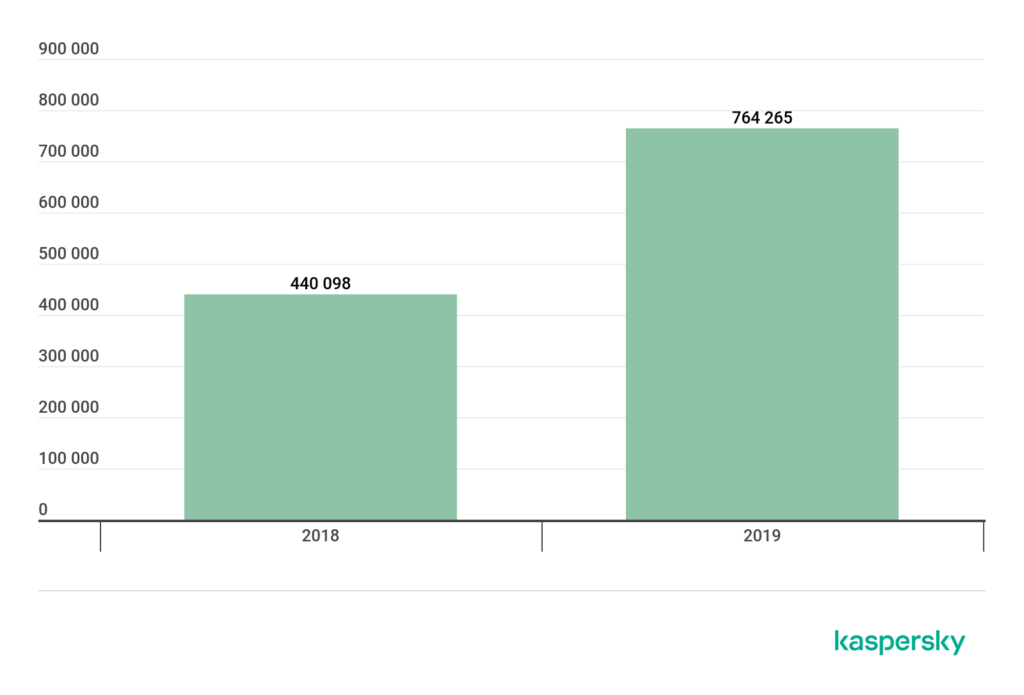
In their 2019 Mobile Malware Evolution Report, Kaspersky states that:
“the number of detected adware installation packages almost doubled from 2018.”
And that’s just one of the threats that target smartphones. Besides advertising malware, there are also financial mobile malware, stalkerware, preinstalled malware, infected links in SMS or instant messages, and mobile ransomware.
It’s undeniable that mobile threats are one of the core reasons why cybersecurity matters in times of crisis, so keep that in mind as you talk to your employees.
5. Brute force and credential stuffing
Cyber attackers have access to hundreds of millions of valid username and password combinations they can use against countless accounts. HaveIBeenPwnd attests to it.
What’s more, a McAfee 2018 report states that:
“Consumers who responded to the survey have an average of 23 online accounts that require a password, but on average only use 13 unique passwords for those accounts. 31% only use two to three passwords for all their accounts so they can remember them more easily.”
Carrying out credential stuffing and brute force attacks is a low-hanging fruit for malicious online actors. It’s just too ripe of an opportunity to pass up.
Under these conditions, you can bet that cyber criminals will make these two types of attacks an essential part of their toolkit whenever the moment is ripe to do so.
For example, when your employees work from home and can’t use company-sanctioned tools to get work done, they might create online accounts for other solutions, choosing weak, reused passwords. Weak credentials stand no chance against automated attacks, which makes work from home security so important, especially as this becomes a reality for almost all businesses.
6. Supply-chain attacks
In times of crisis, small and medium businesses are the most vulnerable, not just from a financial perspective, but also from a security standpoint.
They don’t have big budgets for security (or any at all!) and lack the specialists to implement necessary security controls. Some of them will cover their basis to ensure compliance with current regulations, but those actions are rarely monitored and updated on a continuous basis.
Some of these small and medium companies may provide your products and services you depend on. Your systems may be interconnected in some way.
That means if they become victims of a cyberattack, the incident may affect your business too.
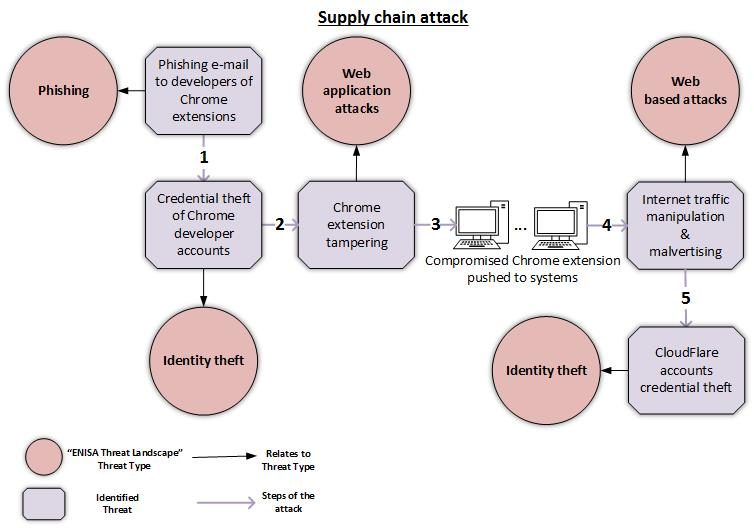
Symantec reported that supply chain attacks increased by 78% in 2019 and the current global crisis is bound to enable this trend to increase.
That’s why it’s so important to audit the software used in your business for security issues, whether it’s apps developed in-house (which makes secure software development fundamental!) or provided by a third-party vendor.
Security measures that help you weather any crisis
ENISA provides a super helpful and practical guide on how to implement minimum security measures in your company. It starts from defining your sophistication level and then progressing to the next one depending on your resources and commitment.

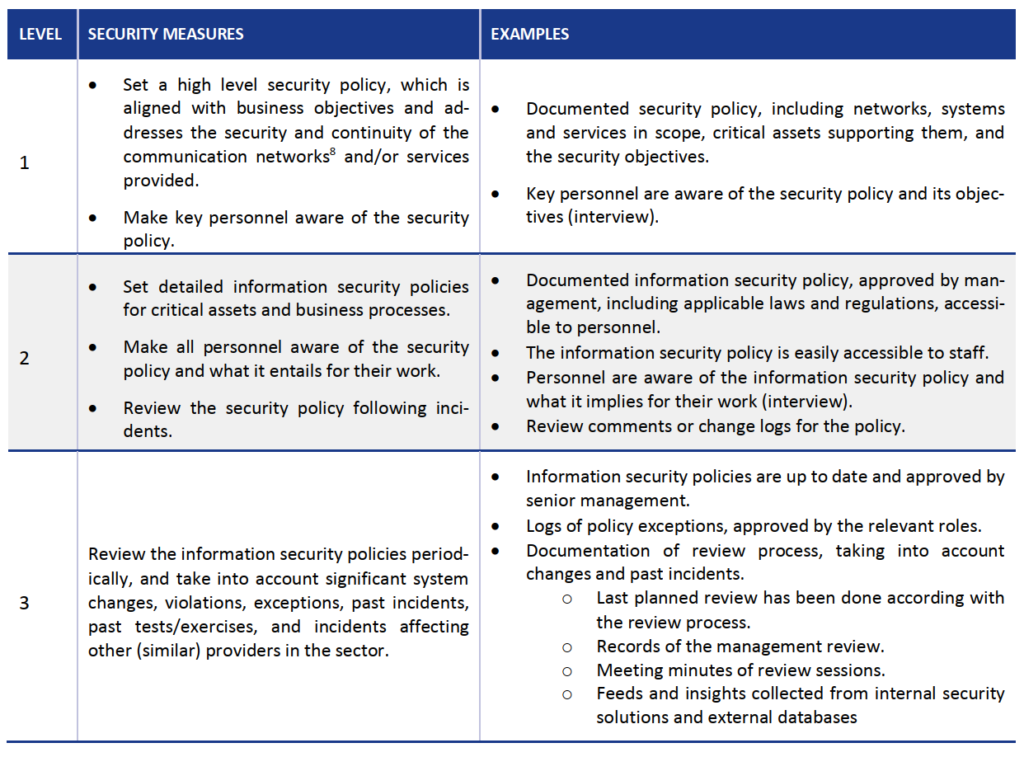
If you’re eager to make your business more resilient through any crisis and ensure its continuity but lack the internal resources to make significant progress, you can always send us a message and we can guide you to your best choices.


