It doesn’t matter if you’re a Hollywood star or just a regular person: no one wants their personal data to be leaked online or made public without their consent.
However, cyber criminals keep finding new ways of accessing sensitive information – including in places you think of as 200% secure and with less effort than you’d imagine. Most of the time, cyber criminals are even successful in their endeavors.
Under these circumstances, is privacy just a myth? The answer could be both yes and no. Can we make it a reality? Definitely yes!
What is privacy? Or: what are the procedures that define what sensitive data is?
As a definition, privacy refers to the protection of personal data or the protection of the “human identity” that defines us as persons in society. In other words, privacy is a way to protect ourselves as individuals in a society.
But how does this protection apply to the digital environment? How do we work with personal or sensitive information online?
Naturally, sensitive data is considered to be of a higher tier than personal data and needs more protection against unwanted access because it is classified information.
In our day to day life, personal data includes a variety of items, such as an individual’s name or email address.On the other hand, sensitive data typically refers to information that fits into one of these categories:
- Information on political views, religious convictions, and racial or ethnic origin
- Information on trade union membership
- Individual identification is based on genetic and biometric data.
- Information about medicine and health
- Information about a person’s sexual preferences or behavior
Things are similar in the online environment.
In a digital environment, sensitive information is data that needs to be protected against unauthorized access and unwanted disclosure in order to ensure an individual’s or an organization’s information security.
There are three main types of sensitive information:
- Personal Information: often known as PII (personally identifiable information), is any data that can be used to steal a person’s identity and is related to that person. For instance, having a person’s passport, ID or visa number makes it simpler to forge official documents. Likewise, knowing their Social Security Number, Personal Identification Number or mother’s maiden name makes it simpler to apply for a credit card in their name. And so on.
- Business Information: Any information that could be hazardous to the firm if disclosed to a rival or the broader public is considered sensitive business information. Intellectual property, trade secrets, or merger plans, for instance, might all be detrimental to the company if they ended up in the hands of a competitor.
- Classified Information: Data that has been purposefully kept secret at the governmental level is referred to as classified information. The level of sensitivity it normally falls under (restricted, confidential, secret, or top secret) places restrictions on who can access the material.
Now that we’ve clarified, from a procedural point of view, what privacy means and how we can figure out what data is sensitive, we can move on to explore what a CDN server is and how it technically stores data.
How does the Content Delivery Network (CDN) server work?
CDN or “Content Delivery Network” is a geographically distributed group of servers that work together to provide fast delivery of Internet content (content like images, books, audio, and more).
To put it short, CDN as a functionality minimizes the distance between the user and the web server content. It stores a cached version of the content in multiple geographic locations. Each location contains a number of caching servers responsible for content delivery to visitors within its proximity.
Note: Browser Caching involves your website’s resources, such as HTML files, JavaScript files, and photos, being downloaded to a visitor’s browser and stored on their local drive. This lowers bandwidth usage and speeds up page loads on subsequent visits.
As functionality, the CDN server has been designed to be secure and prevent DDoS (Distributed Denial of Service) attacks and data exfiltration if the server is properly configured.
Vulnerability in Discord: Sensitive Information Leak!
On March 8th, 2022, I reported a vulnerability to Discord whereby I could extract sensitive data from their application:
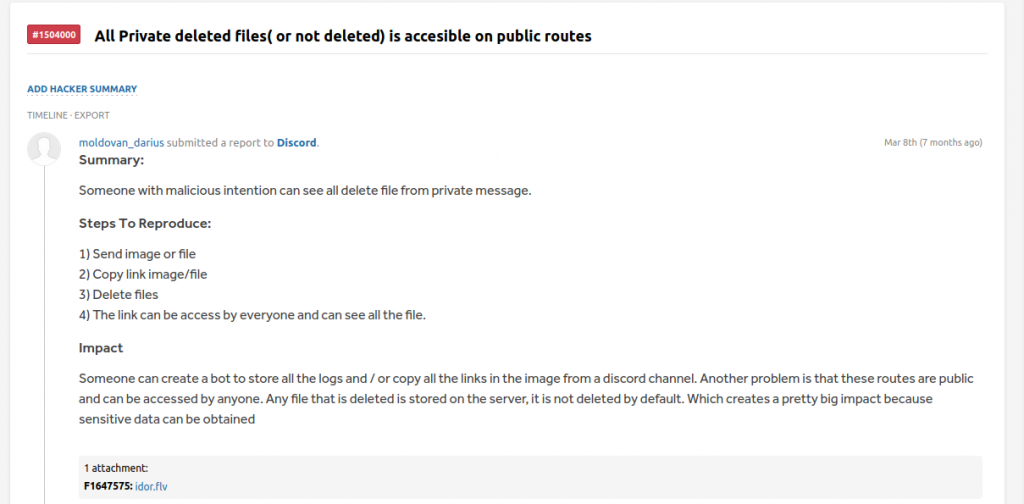
There have been mixed opinions whether this leak is sensitive or not. However, this specific incident is what prompted me to delve into the subject of privacy and how we can protect our data online.
According to the official website of the Discord application: ”Discord is a free voice, video, and text chat app that’s used by tens of millions of people ages 13+ to talk and hang out with their communities and friends.
People use Discord daily to talk about many things, ranging from art projects and family trips to homework and mental health support. It’s a home for communities of any size, but it’s most widely used by small and active groups of people who talk regularly.
The vast majority of servers are private, invite-only spaces for groups of friends and communities to stay in touch and spend time together. There are also larger, more open communities, generally centered around specific topics such as popular games like Minecraft and Fortnite. All conversations are opt-in, so people have total control over who they interact with and what their experience on Discord is.”
Identifying the vulnerability is very simple: sensitive data can be accessed directly from the CDN server based on a series of IDs. Once the length and format are predictable, a person has a pretty good chance to get sensitive data and monitor the person in question.
Another option is to use an Insecure Direct Object Reference (IDOR) vulnerability that allows us to pivot to a specific user. For example, if we send a picture in a private chat, we force the application to display the picture in the web browser without authentication.
Note: Data leakage due to Insecure Direct Object Reference (IDOR) Vulnerability – the application authorization functionality does not prevent one user from gaining access to another user’s data or record by modifying (or by direct access of) the key value identifying the data.
I used this method to expose the Discord vulnerability. The steps in this specific case are as follows:
a. Sending the picture:

b. Force the browser to open in private instance the image which is located in the CDN server:

As we can see, we can access the image from a private conversation in a public environment. Because the CDN server is public to all visitors, that means all images, pdfs, videos, and presentations/projects can be public and accessible to all people.
c. Further proof is the image below where I obtained a pdf containing sensitive information:
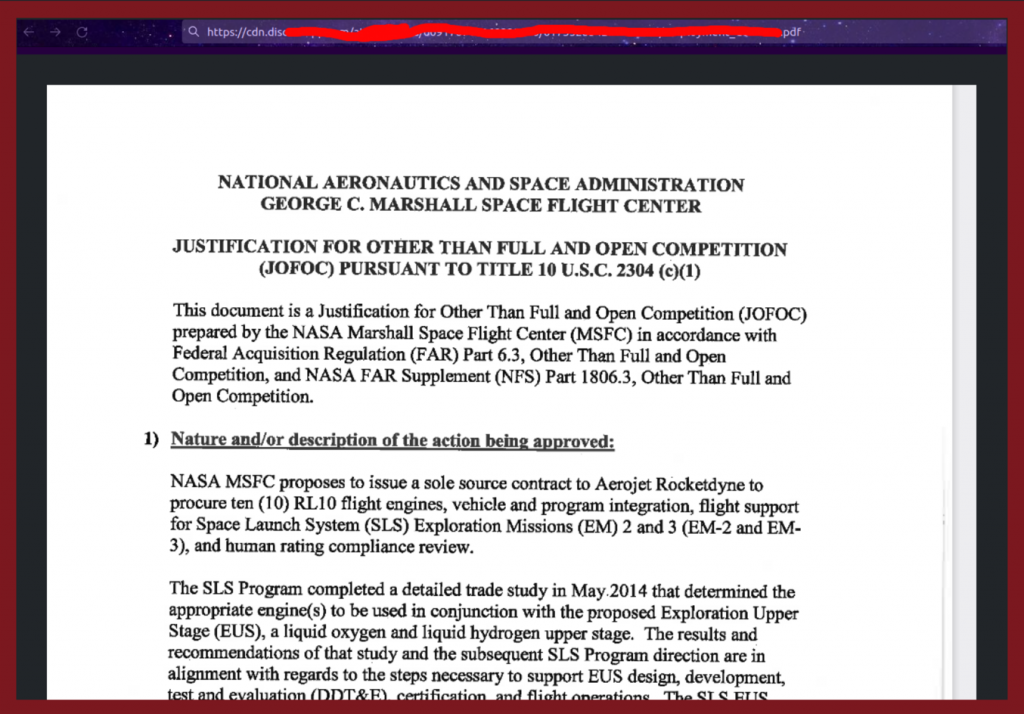
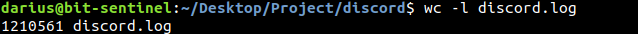
d. Finally, I managed to extract 1210561 URLs with personal data in the last test.
The vulnerability was reported to Discord on the HackerOne platform, but the Discord staff was uncooperative and refused to respond to messages.
Moreover, the vulnerability has not been yet fixed and dangers are still lurking for the unaware or untrained. As you have seen in the example above, the data – whether sensitive or not – was rather easy to be accessed, without expensive or sophisticated tools. Truth be told, this is the reality in cybersecurity: there is no need for overly complicated methods and resources to launch a successful attack. In the face of such risks, we recommend organizations and individuals alike a series of measures to keep their data safe.
10 best practices about privacy principles and their criteria
1. Management
The organization defines documents, communicates and assigns accountability for its privacy policies and procedures.
2. Notice
The organization provides notice of its privacy policies and procedures. The organization identifies the purposes for which personal information is collected, used, and retained.
3. Choice and consent
The organization describes the choices available to the individual. The organization secures implicit or explicit consent regarding the collection, use, and disclosure of personal data.
4. Collection
Personal information is only collected for the purposes identified in the notice.
5. Use, retention, and disposal
The personal information is limited to the purposes identified in the notice the individual consented. The organization retains the personal information only for as long as needed to fulfill the purposes, or as required by law. After this period, the information is disposed of appropriately.
6. Access
The organization provides individuals with access to their personal information for review or updates.
7. Disclosure to third parties
Personal information is disclosed to third parties only for the identified purposes and with the implicit or explicit consent of the individual.
8. Security for privacy
Personal information is protected against both physical and logical unauthorized access.
9. Quality
The organization maintains accurate, complete, and relevant personal information that is necessary for the purposes identified.
10. Monitoring and enforcement
The organization monitors compliance with its privacy policies and procedures. It also has procedures in place to address privacy-related complaints and disputes.
Protect your data in an online environment!
In order to protect ourselves online we should keep in mind the following tips:
- Use a password manager to create and remember unique, complicated passwords for each account.
- Additionally, remember to implement two-step authentication for your online accounts whenever it is feasible. This choice is offered by most banks and significant social media platforms. Two-step authentication involves two steps, as the name implies: inputting your password and a unique access code afterwards.
- Protect your Web Browsing activity because every internet action is tracked by businesses and websites. Your location, browsing history and other data are collected by every advertisement, social network button and website. The data collected reveals more about you than you might expect. You might think you already are two steps ahead for never tweeting about your medical problems or sharing all your -beliefs on Facebook, for instance. Chances are that the websites you visit regularly provide all the data advertisers need to pinpoint the type of person / customer / audience you are. This is part of how targeted ads remain one of the Internet’s most unsettling innovations.
- Use antivirus software on your computer and keep it updated.
- As a company, it is recommended to have regular security audits (Vulnerability assessment and Penetration Testing etc.)
- Use protection technologies, such as firewall, WAF cloud services, periodic backups, and monitoring agents linked to a SOC (Security Operation Center).
To put it bluntly, here is no absolute security. There will always be security breaches, new vulnerabilities, scams, and so on. But that doesn’t mean our hands are forever tied. The interesting part is how we deal with such problems and how well prepared we are. The “it will never happen to me or I don’t need to be audited anyway as I don’t have any personal data” mindset won’t do anyone any good, despite its unfortunate popularity. The crucial thing is that we each implement security measures, both as a company and as an individual, because technology is already part of everyone’s life – and it’s here to stay.
Vulnerability timeline
- The vulnerability was reported to Discord via the HackerOne platform on March 8, 2022, with the title All Private deleted files (or not deleted) are accessible on public routes.
- Discord support closed the report as Not Applicable and added the following “Thanks for reaching out. When messages are deleted we queue up deletions for attachments stored alongside messages. These are processed on a delay, and will happen usually within an hour. Due to various levels of caching, including caches on browsers, you may see content after deletion for up to a year (browser cache) or a day (cdn cache).”

(The test was conducted in incognito mode which does not store browser cache or cookies; and the Discord staff said I can see data after one year of deletion, so how was everything possible? It’s a bit confusing, isn’t it?).
- I asked again what happens with the private data which is not deleted, as it is not ok to be accessible in a public environment (IDOR vulnerability).
- They never answered back…
- Unfortunately, I’ve also had my reputation lowered for this vulnerability.
Where to and what’s next?
If you want to learn more about the topic and improve your cybersecurity skills, you can follow CyberEDU on Facebook, Twitter and LinkedIn. Moreover, if you are a student interested in pursuing a cybersecurity career, make sure you explore the opportunities that UNbreakable Romania has to offer.
UNbreakable Romania is an end-to-end cybersecurity educational program for high school and university students in Romania. Through its activities, UNbreakable provides an X-ray and visualisation of the level of cybersecurity skills nationally. UNbreakable’s mission is to bring together students who are passionate about cybersecurity, so that they have all the resources required to develop the necessary skills to become good cybersecurity specialists. It also provides a competitive environment that encourages collaboration and experience exchange. This way, UNbreakable is actively participating in bridging the cyber security workforce gap locally and internationally.
About the Author

Darius Moldovan (T3jv1l)
Passionate about application security, Darius currently works as a Penetration Tester at Bit Sentinel. He is also Cyber Security Tournaments Manager & Security Labs Author at CyberEDU. In his spare time, he participates in the Synack Red Team in private bug bounty programs or explores challenges in the area of reverse engineering and exploit development.
In the past, Darius has been one of the authors for UNbreakable Romania 2020, 2021 & 2022, DefCamp Capture the Flag 2020, 2021 & 2022, and Romanian Cyber Security Challenge (RoCSC) 2021 & 2022.


