In July 2021, the 1 CF Witting Hospital in Bucharest was a victim of a ransomware attack that heavily targeted the institution’s servers. Similar attacks happened in the summer of 2019 at four other hospitals throughout Romania. In August 2021, attackers targeted and blocked the vaccination scheduling platform in Italy, demanding a generic ransom. Users were unable to access the system and book their place for a vaccine. You’ll see later on that ransomware is one of the top 3 cyber attacks that happen in healthcare.
What these attacks have in common is that the only significant damage was the disruption in these institutions’ activity. Some might say this is not that life threatening; yet it is dangerous.
Another thing all these situations have in common is the proof that a cyber attack is more a matter of “when” rather than a matter of “if”. Cyber criminals will target organizations sooner rather than later because they unknowingly provide: easy access into their valuable database, vulnerable or outdated systems, untrained staff (most of the time), and a potential financial and professional satisfaction for a cyber criminal. And the consequences can be unimaginably severe. According to the IBM X-Force Threat Intelligence Index, healthcare was the seventh most attacked industry in 2020 worldwide, going up from tenth place in 2019.
So, what are the vulnerabilities that make health institutions such inviting targets for cybercriminals?
1. Data-rich, yet outdated systems
Technology is constantly evolving and so are cybercriminal tactics. Unfortunately, digitization and the adoption of new technologies and practices, especially cybersecurity related, are very slow processes in public institutions. This is quite worrying, especially in the case of healthcare organizations, where lots of private data and even human lives are at stake.
Hospitals handle a lot of private information belonging to their patients. However, they do not have basic cybersecurity expertise (cybersecurity roles in health systems take 70% longer to fill than other IT jobs), strategies or regulations. Also, they do not have proper prevention or detection measures, such as antivirus programs installed – let alone updated -, or proper incident response plans.
The financial gains of accessing and selling data are colossal and enough of an incentive for malicious actors to exploit this security weakness. A 2021 IBM analysis, Cost of a Data Breach, shows that responding healthcare companies registered the highest average breach costs at $9.23 million — compared to the previous study, this is a $2 million increase.
2. Staff: brilliant, yet untrained in the face of digitisation
Protecting sensitive data is not just a job for specialized softwares. It should be a universal responsibility of the staff to understand elementary cybersecurity notions, how and why malicious actors develop and deploy attacks against their institution or why protection is mandatory. Needless to say, they also need to be aware of their role as a key actor in the unfolding of such an attack. The focus should be at least evenly distributed between protecting lives and protecting data. Unfortunately, according to a 2018 Accenture survey, 1 in 6 healthcare employees are unaware of cybersecurity training at their organizations.
Human error remains the number 1 security threat in any business, causing 95% of breaches in 2021. The recent rise in telehealth practices, encouraged by the COVID-19 regulations, was an opportunity for healthcare professionals to work remotely. Sometimes, they even used unmonitored or poorly secured devices. Under these circumstances, the risk that untrained staff poses to the healthcare system is even higher. To fix this situation, there are some tips on how to help them collaborate securely.
3. Complex, yet easily broken into infrastructure
Hospitals, clinics and laboratories alike work with an enormous number of connected medical devices. This number has increased along with the advances in wireless technologies. The bigger the organization, the riskier the network. Add an untrained staff and a deficit in cybersecurity specialists and you’ve got yourself a strong base for a cyber attack.
The cherry on top is the outdated equipment that is still in use. Approximately 60% of medical devices are at their end-of-life stage, with manufacturers not supporting any upgrades. This further translates into a higher number of vulnerabilities – more exactly, around 6.2 per medical device. The internet of medical things (IoMT) does wonders for patients as far as healthcare services are concerned. Yet, there is still room to improve when it comes to securing a network of devices coming from different manufacturers.
Taking everything into account, how exactly do malicious actors disrupt the healthcare system? Here are top 3 cyber attacks in healthcare
Essentially, from hospital computers and patients’ monitoring devices, threat actors can spread their attacks towards any available target. Moreover, given the increased connectivity among devices, these attacks can span to third party service providers or other medical vendors as well. The attacks come in many shapes and sizes. Here are top 3 cyber attacks that happen in healthcare.
1. Ransomware
Out of all possible types of malware, ransomware has seen the biggest growth in recent years. Healthcare has been seriously hit by such attacks – just quickly review the examples at the beginning. And we’ve seen health institutions in Ireland and in the US falling victim to ransomware, too.
The reasons malicious actors use this tactic are simple: it is easy to learn, there is no need for expensive tech or for any sophisticated setup. Not to mention that it is very profitable as well – especially since a lot of payments are requested in cryptocurrency. Besides, organizations prefer to pay the ransom rather than fight back.
According to a worldwide survey conducted in January and February 2021, 34% of healthcare organizations paid the ransom to get their data back. Only 65% of their data was actually restored. The same survey shows that players in the healthcare sector prefer to pay the ransom due to the fact that they need to ensure the continuity of their activity. The long-term effects of such a decision, however, can be harmful. It encourages threat actors to plan other attacks and extort large sums of money. This could further damage healthcare budgets and activity.
A more effective way for health institutions to access their data again would be to have it previously stored on at least one offline device. The staff should assume from the very beginning that a ransomware attack will take place sooner or later. Healthcare organizations, too, should install strong anti-malware and anti-ransomware software. Furthermore, they should prepare proper recovery plans in the event of such an attack.
2. Phishing
22% of all data breaches in 2020 involved phishing attacks. Phishing is closely tied to ransomware: one simple click on a deceiving link can affect an entire organization. This long-established social engineering tactic has become a trending attack on the healthcare system. It is the main channel that delivers ransomware. The pandemic did a very good job in intensifying worldwide fears and weaknesses. Online criminals jumped at the opportunity to take advantage of them, even as hospitals were struggling under the weight of infected COVID patients. Many of the attacks that have targeted the healthcare system in 2020 and 2021 have relied heavily on email, given that this is the main channel of communication between professionals.
But did you know that attackers can impersonate and discredit healthcare organizations as well? Another way the pandemic was taken advantage of in this regard is COVID-19 related phishing attempts, from emails asking for proof of vaccination, emails from healthcare institutions, to fake discounts for COVID tests.
A proper protection against phishing attacks is to create a basis for every organization’s cybersecurity hygiene. In addition, institutions should follow a strict set of rules that help them prevent, detect or even respond to such attacks. Training and tests that replicate real life situations could be helpful for the staff to understand the mechanism behind malicious emails. That implies: how they look, how urgent or worrying they sound, what kind of suspicious links or documents they have attached, who sends them, how to verify them. And these are basic rules that could help institutions eliminate phishing from the top 3 cyber attacks in healthcare.
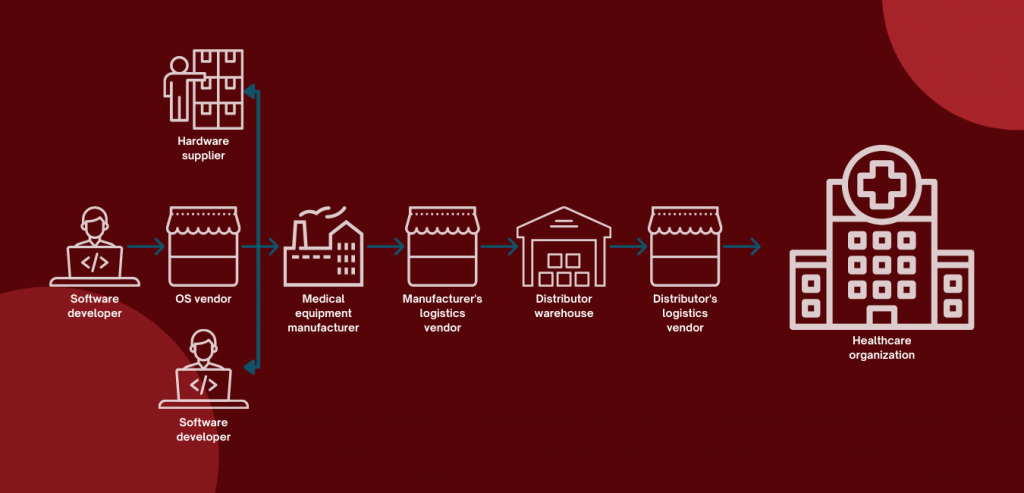
3. Supply chain attacks: the danger in Remote Patient Monitoring (RPM) devices
What happens if attackers don’t target the hospital directly? What if they go for one of their providers instead? Maybe the medical equipment manufacturer. Or maybe further back than that.
We usually tend to think about cyber criminals stealing and selling data for financial gains. However, another dangerous area is related to remote patient monitoring devices. Any malfunction of such a device can be life threatening. It has been proven that this malfunction can be caused remotely. Even as far back as 2007, US Vicepresident Dick Cheney had the wireless functions of his heart defibrillator uninstalled in order to prevent any remote attack that may provoke a cardiac arrest. Concerns continue to exist. Even other medical devices can be targeted, such as insulin pumps, for example. Attackers can deplete their contents with just a push of a button, metres away, without any information about the device.
Malicious actors can deploy attacks in various ways. Consequences can be devastating. There can be delays in patient care, failures to access vital patient information or control the equipment that manages a patient’s health functions. All these jeopardize overall safety and life. As a result, medical devices manufacturers should produce them based on an infrastructure that follows cyber security rules and practices and that allows for periodical reviews of security vulnerabilities.
Even in the healthcare industry, there are many entry points for various perpetrators that can target hospitals, third party vendors or service providers. Any attack on one participant in this supply chain can bring the other one down. An ENISA report shows that supply chain attacks are expected to increase four fold in 2021 compared to last year. Therefore, we expect threat actors to take advantage and reach potential targets in the healthcare system as well.
What can health organizations do to minimize the risks of cyber attacks?
Perhaps the most important thing health organizations need to remember is that any cyber attack targeting them is not only data sensitive, but life sensitive as well.
As a result, protection measures should be taken into account. A lot of pressure is coming from the European Union. The NIS directive requires healthcare organizations, among other operators of essential services, to have the right security controls and processes in place. Failure to comply with these requirements may lead to healthcare institutions being fined with up to 5% of their turnover.
Here are 5 main directions that these institutions can follow in order to build their cyber-resilience and avoid falling victim to the top 3 cyber attacks in healthcare:
- Invest in regular cybersecurity training for their employees to prepare one of the most important security layers in any organization.
- Establish clear procedures, protocols, strategies and user security policies that can be easily followed when handling physical and virtual information and networks; verify and update them regularly.
- Create an incident response plan and promote an incident response culture.
- Know your weak spots and use professional services to carry out simulations and identify vulnerabilities.
- Secure their perimeters, networks, endpoints, applications, data and mission critical assets.
Remember that cybersecurity is similar to medicine, it’s always better to prevent a cyber attack rather than recover from one. With the proper measures in place, any organization can ensure a strong basis for the proper cyber security hygiene.


