Cybercrime is becoming more and more aggressive with an increase in the use of extortion and the current WannaCry ransomware attack is like a wake-up call for businesses. It demonstrates that computer cyber-related fraud is a more prominent threat than more traditional crime types. There are both opportunities and challenges within businesses for risk mitigation. Everyone must realise that in the current environment, no organisation is immune to a cyber threat.
WannaCry was released online on May 12, 2017, but researchers showed it relies on a vulnerability in Microsoft Windows SMB Server which is patched from March 14 in MS17-010 Security Bulletin.
How it Works
WannaCry first spreads through phishing e-mails or fake ads. Once a victim is infected, it starts looking for other potential victims in the same network which are vulnerable to MS17-010, a vulnerability which is supposed to be first discovered and used by NSA.
The ransomware drops and launches a Tor client on the infected machine to anonymize its communications with the attacker’s servers. Tor helps the criminals hide their attack infrastructure and also prevent the interception of encryption keys or Bitcoin payment confirmations that the victim’s endpoint would send.
The malware downloads & launches a number of different executable files on the infected endpoint, each of them carrying a different function. The most important part of the encryption is that encompasses 160 different file extensions to make sure the message is clear. WannaCry will encrypt files with the .wcry/.wncry extension.
Then, it ensures that the user can’t access previous copies so the malware deletes all shadow copies from the endpoint.
Significance & impact
WannaCry strikes hard and the attack has become so extensive because it abuses various security breaches in Windows SMBv1 and SMBv2. Microsoft launched a warning on this topic in March when they also recommended an update for this critical security breach but seems like the users didn’t took it seriously.
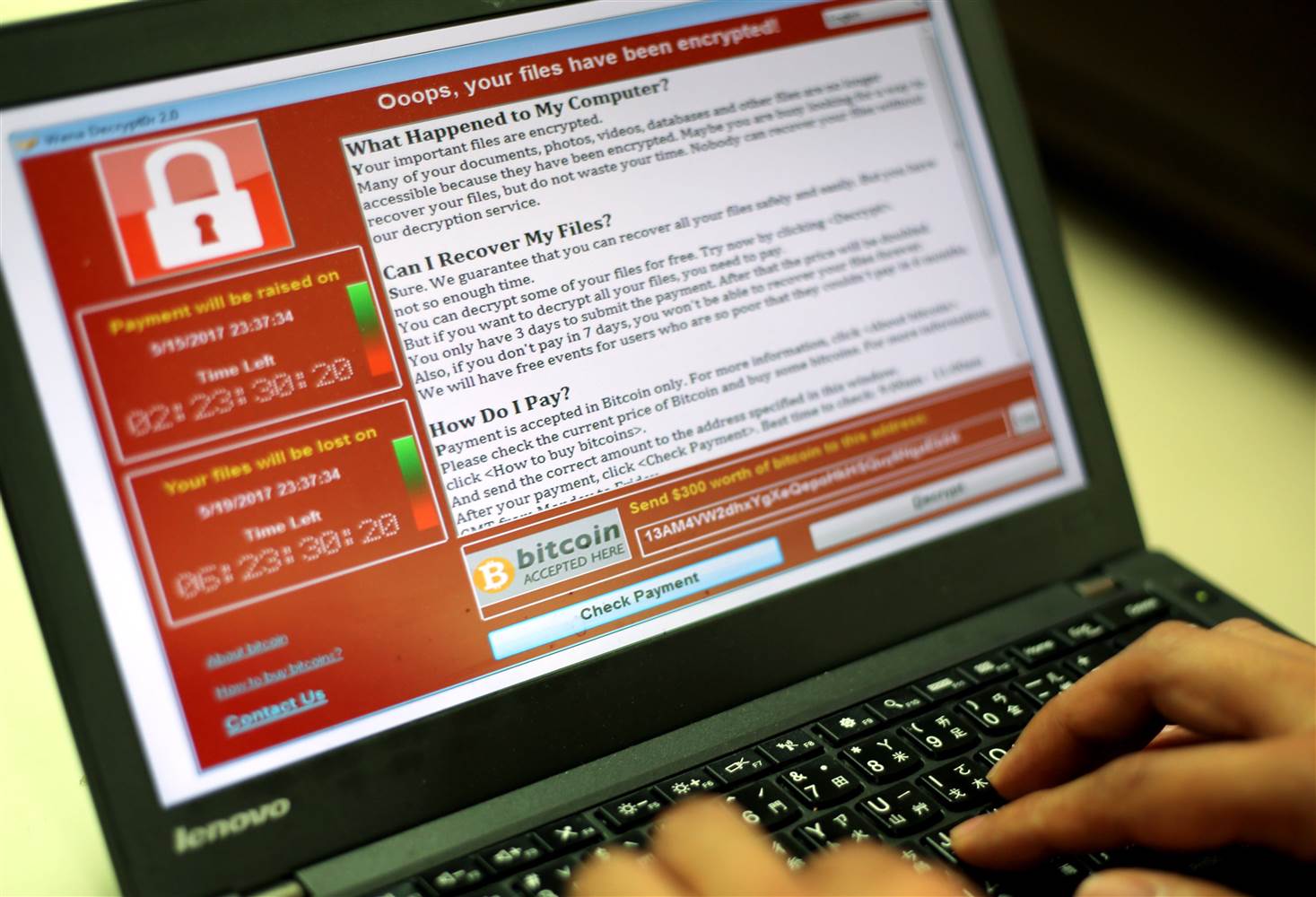
For the attacker, it is the proper playground to launch the WannaCry ransomware and to let it spread in infrastructures all over the world. It spreads easily, silently and remains invisible to users only until it unveils itself as ransomware, threatening users that all their files have been encrypted with a key known only to the attacker and that they will be locked out until the attacker will receive the ransom of $300 using the cryptocurrency Bitcoin. If the ransom is not paid in the first 24 hours the amount will double and eventually they will make the data permanently inaccessible.
So far, WannaCry has hit more 250,000 devices from 100+ countries including hospitals, rail systems, telecommunications and courier services including hundreds of businesses and individuals worldwide.
How to prevent WannaCry Ransomware infection?
In order to prevent infection with WannaCry you must disable SMBv1 & SMBv2 on your system, update your antivirus and the operating system. Moreover, you should backup your data on an offline storage device. Please have in mind that all Windows operating system, up to Windows 10, are vulnerable to this particular vulnerability. Microsoft released a patch also for Windows XP, Windows 2008 or Windows Server 2003.
How to prevent & minimize Ransomware impact?
- Do not pay! You will support criminal activities and also you might not receive the files back.
- Create a clear overview of all your data including a risk assessment: what kind of data my business has and where and how everything is stored exactly.
- Always use backups: make sure to keep at least one copy of every new information that enter into your company everyday and consider using offline backups (without any internet connection).
- Segment your network & store critical/sensitive data under permanent monitoring: it’s recommended to make a data prioritization from your infrastructure, create categories and identify what information is critical to your company and then store it in a separate location than your other data. Never keep all your data in one place that can be accessed by anyone in the company.
- If you are a decision maker in the company, you should consider having a vulnerability assessment or penetration testing service at least once a year.
- Threats may come from third parties: make sure to analyze all possible computer threats from your vendors; ask what security risks each device or application has before you make the acquisition.
- Develop data breach & incident response procedures so you will know what to do when the inevitable happens. You need know a cyber security company to help, you need to have templates and procedures how to communicate with your employees, customers and suppliers and announce the potential breach.
- Train your employee using Social Engineering Services. People is the weakest link in the chain. Although WannaCry spreads via a Remote Code Execution vulnerability, the malware gets into your network first with “the help” of unexperienced employees.
- Keep your system, application and antivirus always up to date.
Keep in mind that getting infected with ransomware or having your infrastructure breached is not a shame, the biggest companies have had breaches over time. It’s all about how you take actions to minimize losses such as customers information, company blueprints or reputational damage.